
5 Steps for Strengthening Cyber Resilience
Authors: Jake Hammacott & Oliver Knapp
Release Date: 26/04/2024
In the modern day, threats to businesses originate almost entirely in the digital world, be that with the aim of stealing identities, or the more basic desire of financial gain. As such, to businesses in this day and age, strong and expansive cyber security capabilities are paramount to their success and protection. This point is compounded by the hard fact that in 2023, 72.7% of businesses were subject to a ransomware attack (Statista), the most common type of cyber attack. Thus showing the importance of being able to prevent and deal with the likely eventuality that you may be part of this statistic.
We at Somerford understand the importance of having strong cyber security and as such have compiled the 5 key points which we think are important to ensuring your cyber resilience. Not only this, but we also partner with multiple companies who offer effective cyber security solutions for aiding you in dealing with these points.
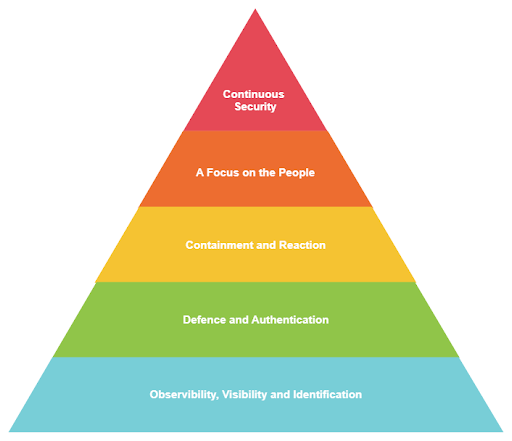
1. Observability, Visibility and Identification
When organisations want to strengthen their cyber resilience, it can be alluring to jump straight into bolstering defences with flashy technologies for their SOC team to utilise. However, issues arise when a new SIEM solution is implemented when no time, effort or thought has been put into identifying and understanding what they’ll actually be reporting and alerting on. A new alerting technology is only beneficial when a concrete plan has been made that details what data the organisation creates and uses, and how it can be manipulated into providing rich, detailed and alertable results. Essentially, the security posture of the organisation needs to be fully understood, documented and utilised before use-cases can be built and brought into these security solutions. There are many ways to solve this issue: data inventories, risk assessments and compliance reporting - just to name a few. By ensuring that the organisation and its data are fully understood and documented before setting through the path to strengthen cyber resilience, the security team will have a much easier time protecting the entire enterprise - which is no easy feat.
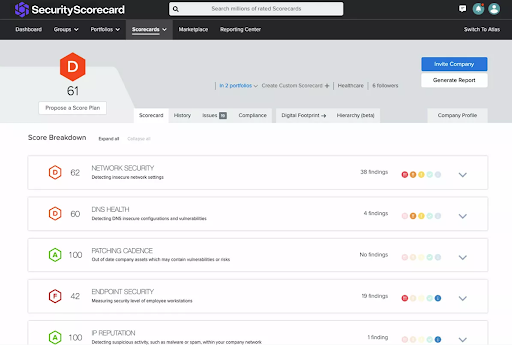
There are many tools, softwares and services available to organisations when creating this initial security posture report. For example, tools such as Security Scorecard are often used to benchmark security performance against industry peers and competitors, providing a detailed account into how the current security posture stacks up against similar organisations. For a user-friendly and effective way to manage and identify risk, compliance and security posture, Security Scorecard is an obvious choice for many. Additionally, they have dedicated resources, blog posts and content that focus on global cyber resiliency, highlighting key issues commonly found within enterprises.
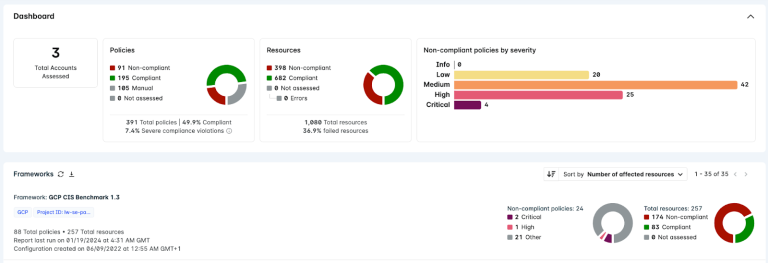
Alternatively, with the ever-growing Cloud-based organisations, cloud-native application protection platforms (CNAPP) are growing in popularity, with solutions, such as Lacework, offering visibility and protection from build-time to run-time. Lacework prides itself on being incredibly quick and easy to utilise, for instance, compliance data is able to be integrated, analysed and reported on within a less than 24 hours. Additionally, Cloud-based organisations are able to generate industry standard compliance reports, focusing on a wide range of specific compliance standards (such as SOC2, ISO27001, etc.). This allows for the full understanding of risks created from cloud configurations, potential weaknesses that could lead to attacks and the opportunity to simplify the, usually stressful and time consuming, audit reporting process. Lacework allows users to generate these reports on demand, meaning progress can be tracked from when you first integrate with Lacework and then daily, weekly or monthly - whatever suits the needs of the organisation.
Additionally, Lacework isn’t limited to compliance data, vulnerabilities are everywhere in applications. Unfortunately, it isn’t feasible or very efficient to completely eradicate and avoid vulnerabilities. Lacework has an emphasis on creating an understanding of which vulnerabilities create the most amount of risk to your cloud infrastructure, allowing analysts to identify and then manage vulnerabilities and decide which of those should be a priority, and which should be an accepted risk.
2. Defence and Authentication
Once an organisation has a strong understanding of their cyber posture, areas of weakness and how these affect data governance within the organisation, the next step many take is to set up defences to protect their infrastructure. This comes in many different forms: SIEM solutions can now be fully leveraged and utilised to alert on potentially risky or dangerous activity, access management tools can be implemented to ensure no user has access to applications that aren't their responsibility and firewall, network and web policies can be adapted and integrated into the work environment. Each of these areas aim to protect a different area of the business as, unfortunately, every single development made into IT infrastructure provides another attack surface for hackers and adversaries to target. It is critically important to provide strong security coverage for every area of an organisation, as a chain is only as strong as its weakest link, spending all of the security resources into web access-control doesn’t mean that an attacker won’t utilise spear-phishing as a technique to obtain initial access into an organisation's infrastructure.
It can seem like an overwhelming task, to protect every area of your organisation, but tools and frameworks have been developed to make the process easier. Companies such as MITRE ATT&CK have developed detailed frameworks that highlight different techniques, tactics and procedures that adversaries can use to attack organisations, and it is widely used within many cyber solutions. For instance, Splunk’s Security Essentials app contains a MITRE matrix that updates to document where your Splunk Enterprise Security use-cases are focusing on, or missing out, specific fundamentals commonly found in cyber attacks:
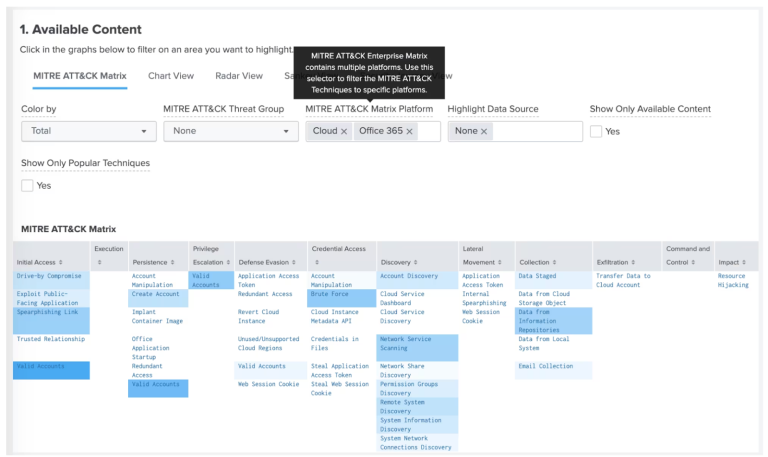
Tools such as these can enable organisations to understand where their SIEM solution is currently alerting on and where new use-cases can be developed in order to protect against most known threats presented by hackers.
When focusing on the safeguarding and security of systems, authentication plays a crucial role in protecting sensitive information. By utilising user verification, access control, identity management and remote access protection, authentication solutions can help protect and prevent attacks, including credential-based attacks and insider threats. With many “different types” of security, organisations can get easy, quick wins that provide another level of security. For instance, in authentication, adding Multi-Factor Authentication (MFA) to high-priority applications can strengthen defences against compromised credentials. Solutions, such as Okta, specialise in simplifying the authentication and authorisation process, providing many functionalities specifically designed for this:
• Single Sign-on (SSO) - Okta enables users to access all applications available to them after a single sign-in, filling out user/password combinations automatically when accessing different apps. This allows for more complex passwords to be used between apps, meaning adversaries attempting access into a specific app will have a harder time using brute force, dictionary and other password guessing attacks.
• Multi-factor authentication (MFA) - as previously mentioned, MFA adds an additional layer of protection by requiring users to provide additional authentication methods, aside from their username/password to access their applications.
• Adaptive Authentication - Okta utilises contextual information, such as device type, location & behaviour to alter authentication requirements based on risk.
• API Access Management - Okta offers API authorisation policies to protect and secure access to APIs.
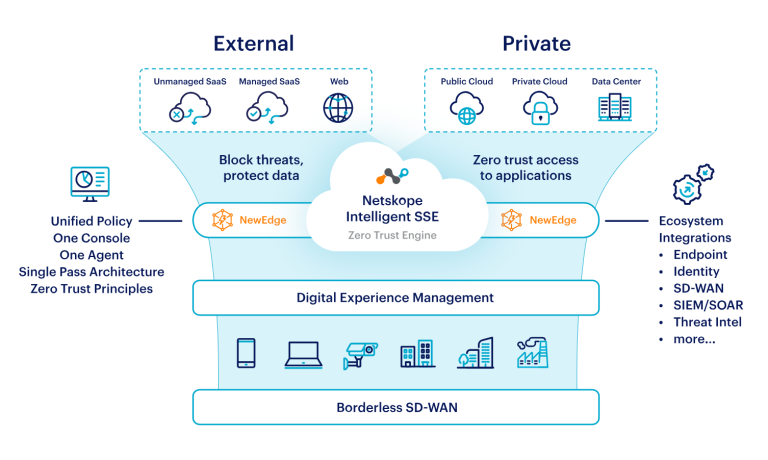
Some cyber solutions focus on solving a variety of risks and threats presented by multiple attack vectors and surfaces. For instance, Netskope acts as a Cloud Security stack, offering protection through visibility, control and security to organisations as they adopt cloud-based technologies. The use-cases and functionality of Netskope seem almost endless, with a keen focus on access, authentication and data-loss prevention, Netskope can often provide the same value as multiple cloud-based solutions without the typical security tool sprawl. From Zero-Trust network access (ZTNA) to their next-generation Secure web gateway (SWG), Netskope aims to provide an extreme development to organisation’s cyber resilience under a single solution, leading to it becoming a market leader in Gartner’s 2023 report on SSEs.
3. Contain Threats and React Appropriately
Now that we’ve covered the identification and defending steps of cyber resiliency, it’s critical to understand and implement correct and appropriate response actions to cyber incidents. Although implementing proactive security measures is great in defending against attacks, it isn’t possible to be completely and entirely defended. Attacks can slip through the cracks of an enterprise’s cyber defence and having a plan in place on how these are approached and dealt with is crucial to minimise damages. Typically, organisations implement a dedicated team that analyse and respond to security incidents as part of a Security Operation Centre (SOC), with many solutions developed with the sole intent of aiding the SOC process.
When utilising a SIEM solution, having a full understanding of what needs to be alerted on, along with response actions required is essential in meeting ticket SLAs. Without a clear plan of execution, SOC teams can find themselves having to deal with large amounts of tickets - leading to ticket fatigue, and clear direction in the result of tickets being created. Ensuring that tickets are dealt with quickly, effectively and in line with SOC policy will ensure that any successful attacks are mitigated as much as possible.
To ensure that tickets and events are contained with efficacy, there needs to be two main things, first a clear understanding and implementation of practices and hierarchy allowing for a SOC or any other type of response centre to work seamlessly. And second, the implementation of tools which allow for these processes to be as effective as possible and which allow for the easy dealing of events in both a logistical and practical sense. For more information on the establishment and benefits of a SOC check out this detailed guide from one of our partners, Splunk: https://www.splunk.com/en_us/blog/learn/soc-security-operation-center.html.
Establishing a solid SOC or response team is usually fulfilled in house, but it is recommended that guidance be sought in order to ensure that you have the best chance at getting it right. The main things to remember when establishing a SOC is to keep a clear order of business and roles within the SOC including architects, analysts and management. As well as defined responsibilities for each of these roles, this then would allow for efficient dealing with threats when they inevitably arise.
Once this has been established, tools should be used in order for the SOC to be built and operate. Utilising a big data and security tool such as Splunk Enterprise Security would allow for each member of the SOC to carry out their role to the best of their ability. Not only this but the response framework itself could be built entirely around Enterprise Security from threat modelling and the use of Splunks bespoke SIEM technology to facilitate rapid investigations and responses through ad hoc searching and a multitude of correlation methods. All adding up to allow every member of the SOC or response team to carry out their role quickly and efficiently and give you the best chance of having a strong and effective response to any events which may occur.
4. A Keen Focus on the People
The weakest point of any cyber environment within an organisation is always going to be the people you have working with/for you. Whilst a computer does not have impulse and won’t press that link or download that ransomware, a human will and as such ensuring that staff understand the best ways to handle attempts at cyber attacks on them, also known as social engineering attacks, is incredibly important. Moreover, attackers understand this point just as well as we do, and as such it is no wonder that 98% of recorded cyber attack attempts originate from social engineering, with 82% of cyber breaches also occurring due to this
(resmo).
The main social engineering methods used by these attackers come in two main forms, either an attempt to steal credentials, that is, trying to make unsuspecting users fill out faux password boxes or giving financial or confidential information to the attacker under false pretences. This then allows the attacker to either assume their identity to gain access, or straight up steal their identity for financial gain. The other method comes in the form of attempting to get these users to click links and download software which would then deploy a cyber attack such as malware or ransomware. The delivery method for both of these methods is through direct communication resulting in the user not realising that the email they just got or the phone call they just had was with an attacker.
This all goes to show that having your users trained to a level where they can easily spot these methods and respond with predefined processes is paramount to your cyber security and company wide cyber resilience. It is also important to note that these attacks occur at all levels of seniority in a business from a CFO to interns and having everyone educated to at least a basic level is the best way to deal with it.
To that end there are many tools and methods which can be employed in order to prevent social engineering attacks from taking place. These being at two different levels, first, preventing the social engineering attacks from reaching the employees in the first place, and second, more importantly, providing education and understanding to the employees on how to spot these attempts.
For the goal of filtering out and preventing emails and other social engineering delivery methods from reaching users, a good option here would be to utilise the webpage blocking and email filtering capabilities found in our partner Netskope’s tooling. With Netskope you can employ their CASB (Cloud Access Security Broker) functionality to monitor the web pages your employees are visiting and block any which match the criteria of phishing sites. With all traffic to and from your clouds flowing through Netskope, monitoring and blocking sites becomes as easy as implementing rules within the Netskope solution.
However the main and most efficient response when considering social engineering is always going to be the training and education of employees, this can be done internally or externally, which we partner with tool providers such as KnowBe4 and Island to provide.
Internal training methods would more than likely be in the form of mandatory training for employees, instructing them what to look out for when it comes to phishing attempts, such as how phishing emails look and the telltale signs that things are not always what they seem, coupled with the testing of the employees to monitor whether this training has worked. This can be done through sending phishing emails internally to the employees, which have been made by the company to see if the employees notice them and if not, this would give a good idea to you that more training is needed.
Whilst internal education and training such as these methods is valuable, we would always recommend going to the experts for social engineering training. Which is why we at Somerford offer the meticulously developed and tested solutions offered by KnowBe4. They are the experts in cybersecurity training for employees, offering simulated phishing attacks and training which has been developed and tested by field experts and solutions for businesses of all sizes. KnowBe4 report that after a 12 month adoption, the average rate for their users falling subject to phishing drops from 33.2% to just 5.4%, which are stats that speak for themselves: https://www.knowbe4.com/.
So in order to truly guarantee cyber resilience in your company, the weakest point must be strengthened, that is your users must understand the risks they face, how to notice a phishing attack, and how to handle it. This can be done through prevention or key training either internally or more reliably, externally through companies such as our partner KnowBe4. Remember to keep a keen focus on the people.
5. Continuous Development
In today's cyber landscape, things move fast, really fast. With methods of attack being changed and evolved every day, being completely secure one week and then the next being vulnerable is not unheard of. As such, being able to consistently update your cyber security to deal with new threats and being prepared to face what may come is incredibly important to your cyber resilience.
The facets we have previously covered form the basis of a strong and overarching cyber security landscape within your organisation, however to truly complete your establishment of cyber resilience, having processes and tools in place which allow for your established security to keep up with the times, as it were, is incredibly important, ensuring that you do not get left behind.
The best method to ensure consistently up to date security would be to implement business wide processes which aim to ensure that there is consistent monitoring of many different data sources which give information regarding the newest security tools and methods and also attacks which have occurred, such as the MITRE ATT&CK framework for example. There is also the need to ensure that these processes are stuck to, be this through the deploying of bespoke tools which run reports on the state of your cyber security on a timely basis or through the employing of staff whose role it is to do this. We recommend using automation tools which produce reports to this end, as this saves both time and money. Tools such as Lacework and Splunk ES have built in features specifically to this end, allowing you to see emerging threats and the best ways to combat them within the context of your organisation.
The key tooling offered by Somerford to assist in the goal of consistent content updates and security being kept at a high standard would come in the form of our partners who offer regular content update and infrastructure monitoring and reporting. As has been previously discussed in this blog, Lacework offers the functionality to run reports which compare your cloud environments to a multitude of frameworks and compliance regulations. These reports can be scheduled to run on a consistent and timely basis, providing you with regular reports on the state of your environments. Not only this but Lacework is constantly updated with new features and developments which suit the current cyber landscape. A key example of this would be Lacework introducing new features looking at Kubernetes security within the context of your environment (see our other blogs for more on Kubernetes) and also their utilisation of the new and exciting behavioural analysis techniques.
This is discussed more in our Lacework blog on the Somerford website. On top of all of this Lacework also is constantly updating its store of CVEs (common vulnerabilities and exposures), further showing how it would help you to keep your security up to date, within the context of your environment of course. Splunk Enterprise Security also has something known as the ES content update which can be installed into your splunk environment which delivers pre-packaged security content and is continually updated by splunk themselves to ensure your security is relevant and up to date when compared to the ongoing list of new threats that are uncovered every day.
Conclusion
We hope that through this blog you have gained a better understanding of how best to strengthen and maintain your cyber security and resilience in an age of relentless cyber attack, helping to prevent you from becoming part of some of the aforementioned quite scary statistics.
We have covered observing and realising the threats to your environments, the best way to defend against malicious cyber attacks and how to contain and respond should they occur. As well as taking a look at securing the weakest link in your cyber chain, the users and making sure all of this is constantly kept up to date and relevant in an ever evolving cyber world. We also covered the tools offered by Somerford to this end and how each of our partners can help you secure your environments at every step.
More Resources like this one:
Somerford's Added Value Explained
Partner & Customer Testimonials |
Business Value Panel Discussion
Partner & Customer Testimonials |
Business Value Panel Discussion







