
What is Lacework FortiCNAPP?
Author: Oliver Knapp
Release Date: 27/10/2023
In essence, Lacework FortiCNAPP is a complete cloud security tool which allows for an incredibly high level of visibility and, as such, control and security across all of your cloud environments. This is achieved through multiple methods which all come together in order to achieve the aforementioned visibility and control.
Lacework FortiCNAPP employs complex machine learning models more commonly known as behavioural analysis techniques in order to keep your data and cloud safe, alongside this.
Lacework FortiCNAPP provides a centralised, web hosted hub of all of your information in the Lacework CNAPP (Cloud Native Application Protection Platform). Here, we will discuss the technology used within Lacework FortiCNAPP, where the value in it really lies and how Lacework FortiCNAPP uses this technology to provide full and competent security to your cloud environments.
Behaviour Analysis
Why use it?
Whilst the aforementioned key benefit of it being relatively lightweight when compared to traditional techniques is an important one, as this allows for faster response and more data to be collected and interpreted. Another key benefit is that behaviour analysis, especially within Lacework, is much more scalable and reliable in the long term when compared to rule based approaches, this is perfect for the massive cloud environments Lacework is intended to be used in.
What's the catch?
This is not to say, however, that behavioural analysis has no drawbacks. The main one is that due to the nature of the detection there is bound to be the issue of false positives. Meaning that events which are not malicious are flagged as malicious, an issue, as this would draw the attention of administrators who believe an issue exists where one does not. Lacework handles this issue with a simple yet effective method which comes in twofold, first is the ability to set alerts which have been flagged as false positive manually, which then the machine learning employed by Lacework FortiCNAPP would learn from and know for next time, this plays into the scalability of the platform which was previously talked about, as it shows that as Lacework FortiCNAPP is utilised it performs better and better. Lacework FortiCNAPP also puts all of the events it flags into context and if it can see that whilst the event happening is not recognised as normal, if all of the other events it works with make sense and nothing bad happens due to the event then it will no longer flag it as an issue. Again something which it gets better at doing over time as the machine learning gets more used to your environment.
I would say it is apt to think of Lacework FortiCNAPP, not as a technology, but as a living entity which learns from your data and advises you on how best to protect your environments, getting better and better as time goes on.
Securing your cloud with Lacework FortiCNAPP
After making the decision to utilise Lacework to secure your cloud you may be wondering what is done on Lacework FortiCNAPP's end. Somerford will work alongside Lacework FortiCNAPP and the customer in order to prioritise and determine all relevant data sources which could be ingested. This will be done through agent scanning, that is, having agents on the cloud environment sending data through Lacework FortiCNAPPk as it is generated in the individual cloud environment, these agents are lightweight and non intrusive and are there to send data to Lacework FortiCNAPP. Agentless scanning is also employed which involves merely connecting your cloud accounts to Lacework FortiCNAPP and allowing it to directly ingest data. It is important to note that Lacework FortiCNAPP works across many different cloud providers and is applicable even if you have an environment which utilises a multi-cloud approach such as having both an AWS and Azure deployment. If anything, Lacework FortiCNAPP's value can be easily realised if there is a multi-cloud deployment as Lacework FortiCNAPP also offers itself as a way to reduce tool-sprawl and greatly helps reduce the added attack surface which is inherent in a multi-cloud environment.
It isn’t just cloud accounts which can be secured, there are a plethora of options provided by Lacework FortiCNAPP which cover all facets of cloud data. A key example of this would be the Lacework FortiCNAPP inline scanning capability, also known as IAC scanning or pipeline scanning, this feature allows Lacework FortiCNAPP to scan your code in development, where any security issues with it, such as a potential backdoor or exposed IP addresses will be alerted on and as such can be fixed before they become a problem. This could have many uses such as pushing out a new app version or even publishing a website.
What are the steps?
The steps for setting up Lacework FortiCNAPP would be first, a call with Somerford Associates where the potential benefits of deploying Lacework would be discussed and explained, then a typical approach is to run a POV (Proof of Value) if required before deploying to production.
Other Key Benefits:
As previously discussed there are many security benefits which are provided through Lacework FortiCNAPP which don’t stop at cloud data.
It isn’t just cloud accounts which can be secured, there are a plethora of options provided by Lacework FortiCNAPP which cover all facets of potential cloud data. A key example of this would be the Lacework FortiCNAPP inline scanning capability, also known as IAC scanning or pipeline scanning, this feature allows Lacework FortiCNAPP to scan your code as it is in development, where any security issues with it, such as a potential backdoor or exposed IP addresses will be alerted on and as such can be fixed before they become a problem. This could have many uses such as pushing out a new app version or even publishing a website.
What is it?
The key technology and methodology employed in Lacework is the use of behavioural analysis, which is a relatively new technology in practice, steers away from the normal methods of data analysis and security. Where traditional methods would see attacks and malicious code being looked at in detail and potential attacks being treated the same, behavioural analysis does away with that weighty overhead of traditional rule based security and opts for a more intuitive method instead.
This is done by establishing an initial behaviour which is then used to compare events and incoming data, this behaviour is established in Lacework FortiCNAPP, through having the software set up in an environment and passively gathering data and looking at what normal data and behaviour looks like to the target environment. This would usually take up to 48 hours, a quick turn around in behavioural analysis terms, which then allows Lacework to establish normal behaviour patterns to compare incoming data, user behaviours and all other metrics it collects to.
IAC Scanning
It isn’t just cloud accounts which can be secured, there are a plethora of options provided by Lacework FortiCNAPP which cover all facets of potential cloud data. A key example of this would be the Lacework inline scanning capability, also known as IAC scanning or pipeline scanning, this feature allows Lacework FortiCNAPP to scan your code as it is in development, where any security issues with it, such as a potential backdoor or exposed IP addresses will be alerted on and as such can be fixed before they become a problem. This could have many uses such as pushing out a new app version or even publishing a website.
Lacework FortiCNAPP offers this to its customers which allows them to secure their code as it is being developed and before it is pushed out to the consumer. The dashboard for this can be seen below:
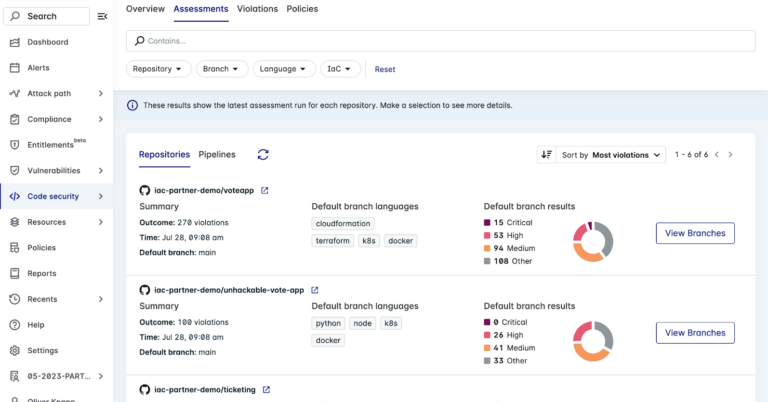
Compliance
Lacework FortiCNAPP also puts an emphasis on the ability to monitor and enforce compliance within your cloud environments, this is very useful to those who are attempting to gain certification or pass audits for certain standards, for example ISO 27001 or SOC 2. Lacework FortiCNAPP allows you to generate reports on the fly which give an overview of your environment in the context of whichever standard is relevant to you, telling you where you are and are not compliant thus providing guidance on how you can make the relevant changes so that you can pass these standards.
Lacework Polygraph
A key part of the lacework platform is the Lacework FortiCNAPP polygraph, this is a visual tool given to the Lacework FortiCNAPP customer which allows them to see all of the connections within their cloud environments and also where data is being sent and connections are being made, this can be seen below. The polygraph can then be explored further through clicking on and zooming in on the different areas of it depending on what it is you want to investigate. The polygraph will also show you which areas the alerts are coming from and where potential malicious events are originating, thus providing an invaluable tool for investigation and understanding events and communication within your cloud environments.
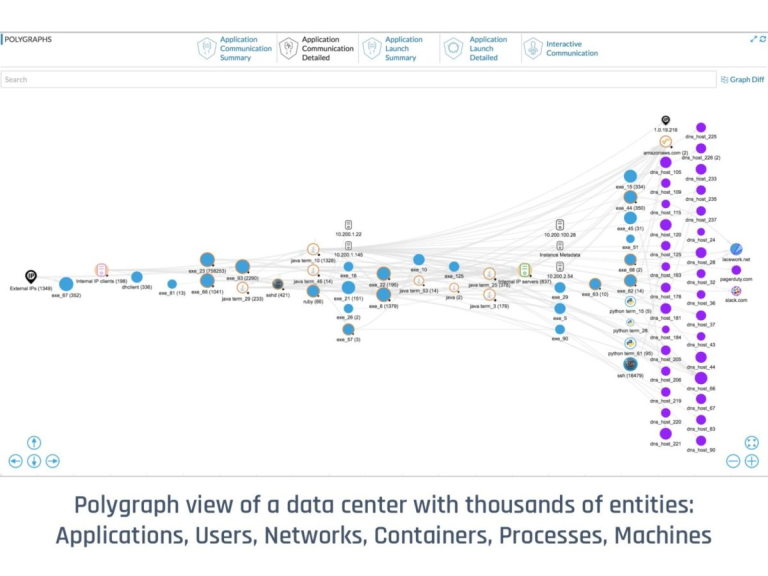
Conclusion
To conclude, Lacework FortiCNAPP is a multifaceted tool which uses innovative technology to provide security to cloud environments. Through the use of behavioural analysis, it provides low overhead and instant feedback to customers through the data it gathers. Lacework FortiCNAPP has many other features which culminate in a complete and comprehensive cloud security tool, solving many of the problems which modern cloud environments have in relation to their security. Not only this but getting set up and running is a simple process and Somerford will provide expert guidance throughout delivery.







