
Securing Salesforce with Varonis
Author: Beth Laws
Release Date: 13/03/2023
Salesforce is one of the most used CRM solutions out there and is a really effective tool used to store customer and prospect data by Sales teams, so effective that it is used by over 150,000 organisations today. Salesforce is often filled with contract data, pricing documents, personal information and a wide range of other types of sensitive information. More than often it goes unknown to IT, Security and Data Protection teams as to what sort of data lives within here and Varonis DatAdvantage Cloud can really help to bridge this disconnect and assist with protecting this data.

Why do attackers target Salesforce?
As Salesforce is a Customer Relationship Management tool, the data stored in here can often be commercially sensitive data. This could be information on sales leads or opportunities, contract data, customers contact information, pricing documentation or even confidential internal information. As well as attackers being aware that such a great volume of sensitive data will be stored in Salesforce, they have cottoned on to the fact that it is not at all uncommon for Security and IT teams to have very little visibility over Salesforce. In fact, sometimes they could even be completely unaware of what type of information is living within Salesforce and who is actually accessing it or potentially downloading this data.
Salesforce created their platform to have many capabilities and user roles, unfortunately with this flexibility comes an incredibly complex and complicated permission model. Permissions can be managed across 4 different levels and specific record-access can be managed through various settings such as role type, sharing rules or manual settings. To add to the complexity, it’s possible to share data with users in your Salesforce Community, which are customers, external users or members of the public who require an account. As a result, it is easy to misconfigure access and accidentally leave data exposed making Salesforce an appealing target for cyber criminals.
How Varonis DA Cloud can help
Varonis can give unique visibility over Salesforce by helping Security teams to classify what type of sensitive information lives within Salesforce and understand who has access to this and what they might be doing with that data.
Identifying Over-Exposed and Sensitive Data
Varonis maps and normalises permissions from Salesforce and other cloud applications and services into a more understandable model, The CRUDS model, where CRUDS stands for Create, Read, Update, Delete and Share. This paints a clearer picture of who has access to this data and pinpoint whether any data is unintentionally exposed to external users or former employees.
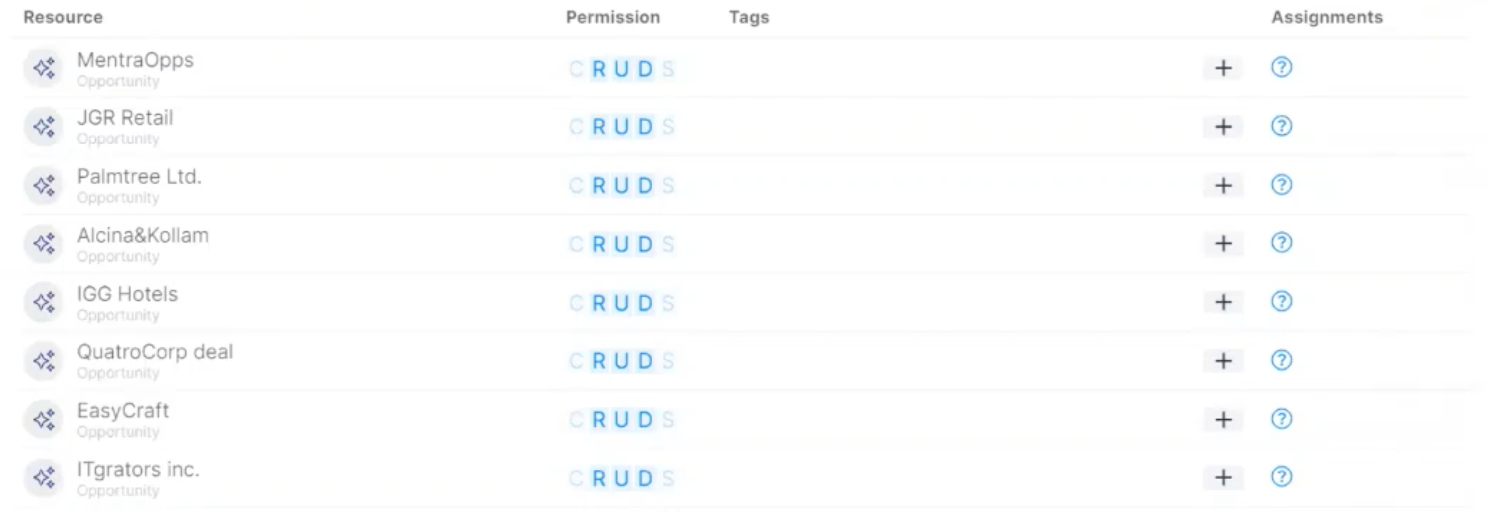
Varonis can classify data to determine whether this is sensitive or not. Patterns and dictionaries along with methods such as proximity sensing are used to identify and detect what type of sensitive data is in Salesforce, helping to understand whether data within here is subject to regulations such as GDPR, or whether something more specific has been identified, as an example, National Insurance number or driving licence details may be detected. It comes with many predefined rules, which can be either enabled or disabled and you can customise these depending on your organisation’s needs as well.
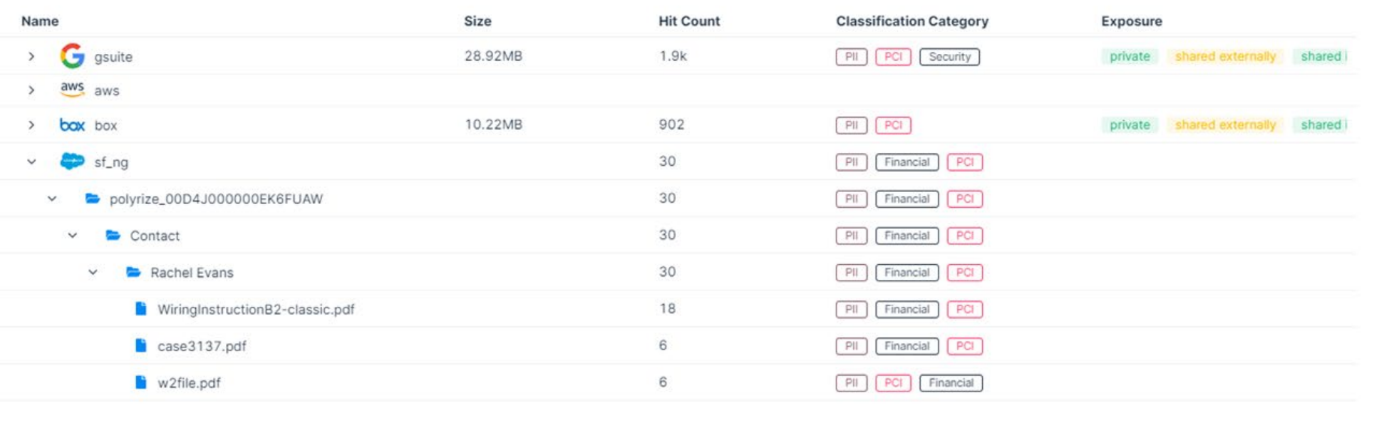
Cross-Cloud Investigations
Varonis links up Salesforce users accounts to other accounts they may have from other cloud applications and services to one identity, helping Security teams to easily monitor and investigate a users activity not just only in Salesforce but across the cloud, therefore reducing cross-cloud investigation times.
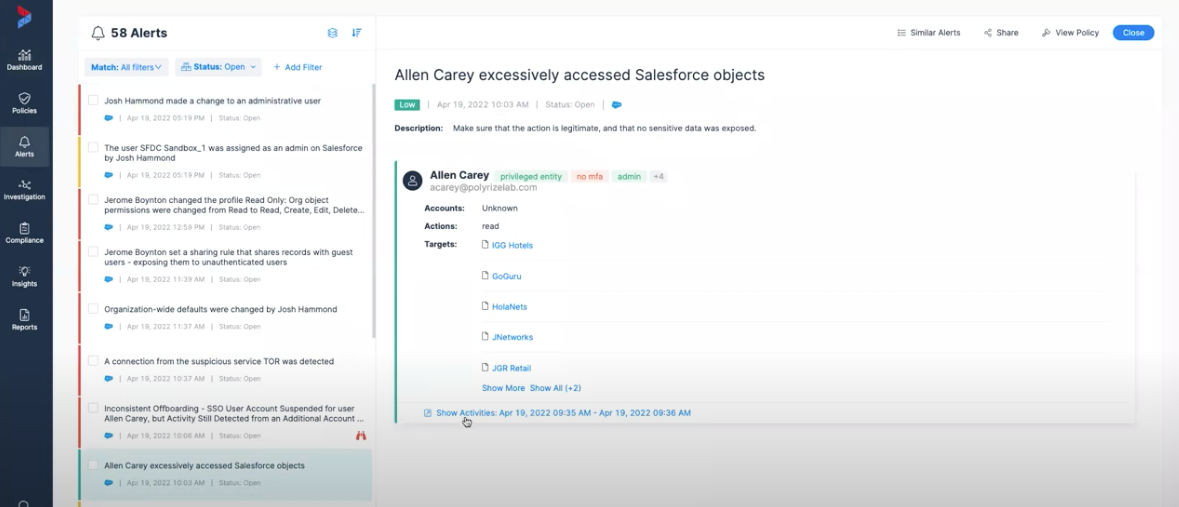
Threat Detection and Alerts
DA Cloud monitors activity going on within Salesforce and can detect insider and external threats and issue alerts to prevent cyber criminals accessing Salesforce. Some examples of these include alerts to detect users accessing an unusual number of Salesforce objects, changes to administrator accounts or changes to sharing rules to share records with guest users and many other Salesforce specific threat models.
More Resources like this one:
Somerford's Added Value Explained
Partner & Customer Testimonials |
Business Value Panel Discussion
Salesforce: How to Defend against Attackers & Rogue Insiders—Ft. Varonis DatAdvantage Cloud (SaaS)
Get in Touch
Contact Beth or the rest of our pre-sales team through our contact form.







