
Legacy PAM - Is a vault really enough in today's modern Threat Landscape
02/07/2019 – Author: Mark Jopling – Lead Security Strategist
For two years in a row Gartner has named PAM a Top 10 security project. Forrester estimates that 80% of breaches involve a privileged identity, and that 66% of companies have likely been breached 5 times or more.
Storing credentials in a password vault as part of Privileged Access Management (PAM) certainly goes some way to securing any modern threat landscape but it could also be argued that it constitutes a single point of failure, governing direct access into any data centre. This carries with it a certain degree of risk.
More often than not cyber-attackers no longer “hack-in” they log in using weak credentials and then attempt to move laterally through a system seeking privileged access to critical infrastructure and sensitive data.
In an increasingly hostile IT environment where privileged credential abuse is widespread vaulting privileged passwords is a must, but can we go further in eliminating an organisation from placing itself at risk of a privilege-related breach?
Considerations
- Do you already have a vault (rule number 1 of PAM club)? If your not vaulting privileged passwords chances are they are written down or stored on spreadsheets!
- Do you implement MFA for local and privileged Administrative access? If not, why not, is it not needed everywhere?
- How many accounts do you have in the organisation and are they all absolutely necessary? The more accounts you have the bigger the attack surface!
- How quickly do you shut off privileged access for employees who leave the company? Insider threat is real, privileged access needs to be instantly revocable.
- Does sharing of root or privileged access to systems or data happen at least somewhat often? It’s vital to properly verify who has privileged access and exactly when.
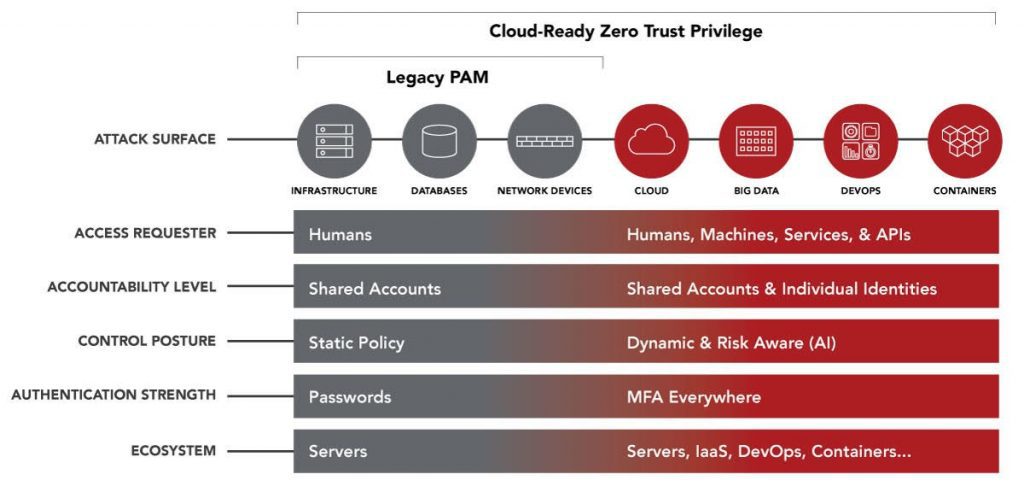
Furthermore, and to add to this list there is the wider consideration that PAM is effectively no longer constrained to systems and resources inside a network such as infrastructure, databases and network devices but that it has extended into an expanded threat landscape that now includes cloud environments, big data projects, DevOps, containers and more.
Where Legacy or password vault only PAM solutions no longer meet this increasing list of considerations organisations can now opt for something else, a Zero Trust Privilege solution that builds on traditional legacy PAM by enforcing a ‘never trust, always verify, enforce least privilege’ approach.
Centrify Zero Trust Privilege Services cloud ready solution verifies who is requesting access, provides the context of any request and gauges the risk of the access environment to help customers grant least privilege access. It can also audit all user activity and make that information readily available.
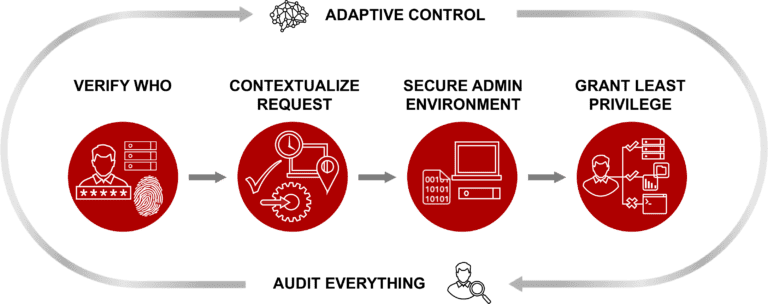
3 Stepped approach to Zero Trust Privilege
- Zero Trust Privilege includes vault solutions for shared accounts and passwords as well as application passwords and secrets, for hybrid and cloud environments.
- If you already have a vault, Zero Trust will go beyond the vault in the PAM maturity model employing Identity consolidation with least privilege. Just-in-time access with just-enough privilege combined with multi-factor authentication at NIST Assurance Level 2 at a minimum for administrative access. Identity consolidation means reducing your attack surface by significantly lowering the use of local accounts on systems and replacing them with federated individual directory accounts that utilise short-lived tokens rather than static passwords.
- If you are already further down the road with PAM, excellent, but there is always more that can be done. It has to be considered that it’s not just humans who are logging in but also applications and service accounts. Your environment can be further hardened with high assurance by integrating with SIEM and ITSM for better insight and governance.
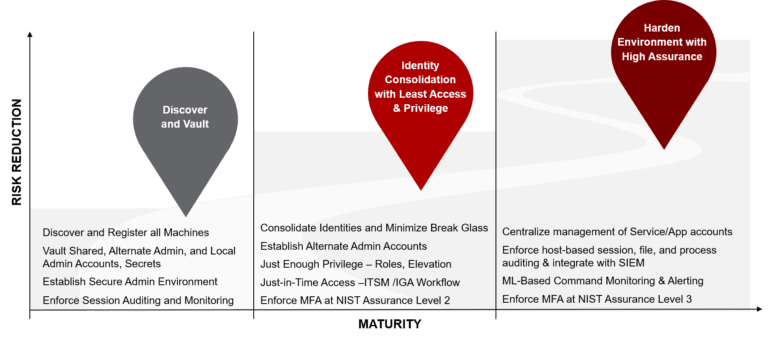
When it comes to effective Breach management exactly how much trust and privilege do you grant?
With the world’s largest financial institutions, Intelligence agencies and critical infrastructure companies being targeted routinely, password vaulting is far from a dirty word but in today’s dynamic environment it is perhaps the belt and braces approach to PAM that will win out.






