
How Advanced Persistent Threats
(APTs) Work
Author: Carl Parker
Release Date: 19/01/2024
What are Advanced Persistent Threats?
When belligerent parties target a business’ data and infrastructure in threatening attacks, the most commonly considered strategy is a fast, quickly spreading virus that searches for valuable information, then retreats as quickly as it entered.
Advanced Persistent Threats (APTs) are quite different.
Click here to register for our upcoming 'Silent Battle of APT Discovery Forum' >
The attackers that utilise Advanced Persistent Threats refrain from quick, explosive jabs, instead preferring to enter networks without fuss, staying silent in the background. From this position of perceived invisibility, the malicious actors behind Advanced Persistent Threats slowly eke out sensitive data with a reduced chance of being compromised.
Whilst Advanced Persistent Threats aren’t the archetypal ‘smash and grab’ cyber assault method, they are nonetheless highly sophisticated and require significant planning and funding. As a result, they are often deployed by well-funded disruptors with ties to nations or organised crime. These attacks may even span years in duration as the assailants bide their time, manually executing and adjusting strategies to avoid detection.
Characteristics of Advanced Persistent Threats:
• Sophistication - APTs employ advanced techniques, often leveraging zero-day vulnerabilities and custom malware.
• Persistence: These threats are persistent, with attackers maintaining a long-term presence within a target network.
• Targeted: APTs are meticulously targeted at specific organisations, often with a strategic goal in mind.
• Covert: APTs focus on remaining undetected for as long as possible, silently exfiltrating data without raising alarms.
What are the objectives of APT Attackers?
The aims for those deploying Advanced Persistent Threats vary, though the strategy has multiple benefits that make it the perfect tool for certain tasks. An attacker might deploy an Advanced Persistent Threat if they aim to gather intelligence over a longer period, maintain control over a compromised system, or conduct political and/or economic sabotage on specific targets. Understanding the motivations behind an attack like this can be a critical element for timely detection and mitigation.
Which techniques do APT Attackers use?
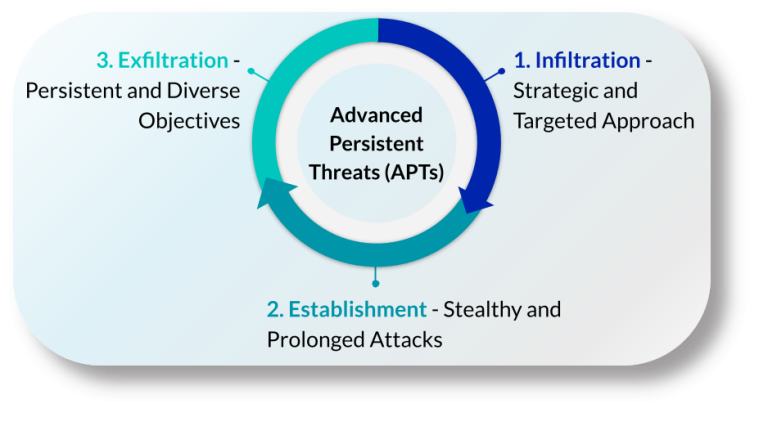
When deploying Advanced Persistent Threats, there are recognisable steps attackers take:
• Reconnaissance: APT actors conduct thorough reconnaissance, identifying potential vulnerabilities, understanding the network architecture, and discovering entry points. They might use methods such as social engineering or scanning publicly available information.
• Network Entry: APTs often start with an initial compromise, typically through methods like spear-phishing emails containing malicious attachments or links.
• Establishing Persistence: Once inside the target network, the attackers work on establishing persistence, ensuring that their access remains undetected and available for a prolonged period.
• Lateral Movement: APTs aim to expand their reach within the network, moving laterally from one system to another. This allows them to explore and compromise more resources, gather sensitive data, or escalate their privileges.
• Data Exfiltration: Attackers may employ various methods to extract valuable data, such as using covert channels, encrypted communications, or carefully timed data transfers to avoid detection.
• Covering Tracks: A key aspect of APTs is the effort to cover their tracks to remain undetected. Attackers delete logs, modify system settings, and erase evidence of their activities to hinder forensic analysis and maintain their access for future operations.
• Sustained Operations: APTs are designed for long-term operations. Attackers might periodically revisit compromised systems, update their attack tools, and adapt their strategies to evade detection by security measures.
How do you defend against Advanced Persistent Threats?
Defending against Advanced Persistent Threats should be considered a two-phase process; prevention in a proactive sense, and detection and response in a reactive sense. To ensure you are adequately covered should an Advanced Persistent Threat be aimed at your organisation, you should ensure that your software is regularly patched and updated to eliminate any potential vulnerabilities in your network. Our partner, Lacework, specialises in identifying vulnerabilities in code and cloud infrastructure, scanning for possible exploits and encourages system or policy updates to reduce the potential impact of an attack.
Other proactive methods include network segmentation and user training. The first of these, offered by our partner Varonis, allows businesses to isolate sensitive data and limit lateral movement. In a properly segmented network, users and their working groups are only able to access the files they require for legitimate business use. This restricts the possibility of Advanced Persistent Threat attackers accessing sensitive information.
User training is also an invaluable tool in securing your perimeter from Advanced Persistent Threats, as it encourages employees to be more vigilant for signs of interference or malevolence throughout their working day. Raising staff awareness on threatening behaviour like phishing emails, file tampering and social engineering are critical. Intensive training courses on these topics are offered to employees across varied industries by our partner, KnowBe4.
If you suspect that you have been breached by an Advanced Persistent Threat, there are still several layers of protection that you could implement, allowing you to counter and remove the threat. The first of these is behavioural analytics from Splunk, which provides wide-scale monitoring of network infrastructure, alerting administrators when it senses an unusual pattern. Keeping a keen eye on any suspicious activity could immediately depose an attacker.
BlueVoyant also offers some similarly effective countermeasures against Advanced Persistent Threats, notably incident response plans, and threat intelligence tools. The former is a dynamic business review tailored specifically for your organisation, which helps you to quickly identify and contain any potential threats when they arise. The latter provides organisations with briefings on the latest cyber threats to stay informed about evolving APT tactics and techniques.
Somerford's Added Value Explained
Partner & Customer Testimonials |
Business Value Panel Discussion
The Unseen Warfare of Advanced Persistent Threats






