
What is a Cloud Security Assessment?
Release Date: 21/06/2022
A Lacework Cloud Security Assessment (CSA) is an evaluation that tests and analyses an organisation's cloud infrastructure to ensure the organisation is protected from a variety of security risks and threats. It provides a detailed analysis of all elements of your cloud environment, including both public and private clouds.
A cloud security assessment can also be used as a baseline for future risk reviews and change management activities.
Why is a Cloud Security Assessment Important?
I have full admin access to a Dev AWS instance.
Whenever I need to demo or test something for a customer I am free to log in and create a device or devices. I used to hit next, next, next, during this process and then I would have my resource(s).
When I did this, I was using the defaults that AWS provide, and their entire process is designed around simplicity and not security.
Upon building a demo platform for a webinar, I previously decided to run a Cloud Security Assessment on that which I had created and found I was in breach of a number of compliance issues. A range of vulnerabilities were documented such as issues with key / authentication methods, I was using defaults for Admin level usernames, my resources were open to the public, etc. Note that these violations aren't solely for AWS, they exist in Azure & GCP too when using default options.
I am not an IaaS expert, I just spun up what I needed, when it was required, and dismantled the infrastructure once done. I understood the surface level vulnerabilities shown during the Cloud Security Assessment based on my prior knowledge of PAM, SASE, etc. but in the output there was a much deeper layer of what was happening behind the scenes within the cloud platform that I myself would never have even known to look for.
Now whenever I build any resource as part of my job, I use a Terraform build script that has configurations hard baked into it that address all of the prior vulnerabilities & compliance issues and to this day when I run an assessment again, I see zero hits.
That is essentially my journey in the IaaS space as a Cloud Engineer.
The above relates to a Dev estate with a maximum of seven servers needed, a mixture of Windows & UNIX and all of which get dismantled on the same day for the session they were used for.
However, what if we scale it up to a Production environment that requires more stringent security protocols?
What if the servers or resources were more permanent?
In my example, I never knew what to look for under the hood in relation to the vulnerabilities I was creating as part of my simplistic build process, so what if said vulnerabilities were also hard baked into Production deployment processes or even on legacy deployed resources?
If build scripts are being used, do they address the compliance vulnerabilities at source?
How would you undertake retrospectively checking a production cloud estate, especially those at Enterprise level?
This is essentially where the Lacework Cloud Security Assessment offering comes into play as it is this that opened my eyes to the problems I was creating.
With this, you essentially allow Lacework access to your Cloud Provider(s), read only, it won't be making any changes, it reviews the logs & configs of your build and reports back on the vulnerabilities & chosen compliance issues it finds.
Now Lacework itself is a much bigger solution and the CSA only relates to a small part of it but to me, it is invaluable to anyone using IaaS these days.
You can choose from a range of compliance standards to choose from, such as:
AWS
AWS CIS Benchmark and S3 Report
AWS HIPAA Report
AWS ISO 27001:2013 Report
AWS NIST 800-171 Report
AWS NIST 800-53 Report
AWS PCI DSS Report
AWS SOC 2 Report
AWS SOC 2 Report Rev2
Azure
Azure CIS Benchmark
Azure CIS Benchmark 1.3.1
Azure HIPAA Report (includes CIS 1.3.1 rules)
Azure ISO 27001 Report (includes CIS 1.3.1 rules)
Azure NIST 800-171 Rev2 Report (includes CIS 1.3.1 rules)
Azure NIST 800-53 Rev5 Report (includes CIS 1.3.1 rules)
Azure NIST CSF Report (includes CIS 1.3.1 rules)
Azure PCI Benchmark
Azure PCI Benchmark Rev2 (includes CIS 1.3.1 rules)
Azure SOC 2 Report
Azure SOC 2 Report Rev2 (includes CIS 1.3.1 rules)
GCP
GCP CIS Benchmark
GCP CIS Benchmark 1.2
GCP HIPAA Report
GCP HIPAA Report Rev2 (includes CIS 1.2 rules)
GCP ISO 270001 Report (includes CIS 1.2 rules)
GCP K8S Benchmark
GCP NIST 800-171 Rev2 Report (includes CIS 1.2 rules)
GCP NIST 800-53 Rev4 Report (includes CIS 1.2 rules)
GCP NIST CSF Report (includes CIS 1.2 rules)
GCP PCI Benchmark
GCP PCI Benchmark Rev2 (includes CIS 1.2 rules)
GCP SOC 2 Report
GCP SOC 2 Report Rev2 (includes CIS 1.2 rules)
With how easy it is to configure (the Lacework / Cloud Platform integration can take minutes) you can be well on your way to identifying issues with your Cloud Platform, any build script issues, legacy configurations, etc.
Details on the integration steps can be found here:
AWS - https://docs.lacework.com/category/integrate-lacework-with-aws
Azure - https://docs.lacework.com/category/integrate-lacework-with-azure
GCP - https://docs.lacework.com/category/integrate-lacework-with-gcp
Once done, and when left for two weeks, the outputs look like the below.
You get a full breakdown of the vulnerabilities identified in your Cloud Platform, broken down by compliance template:
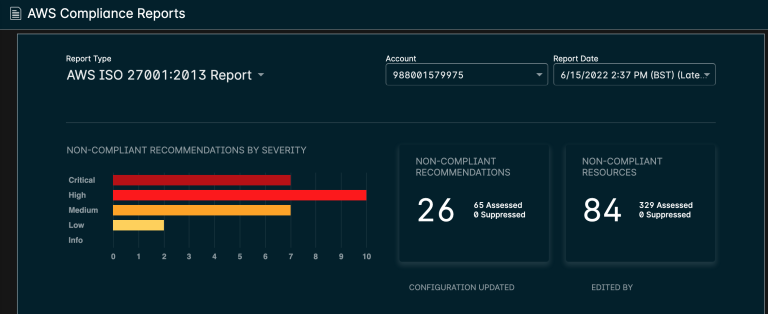
And a breakdown of each individual compliance issue:
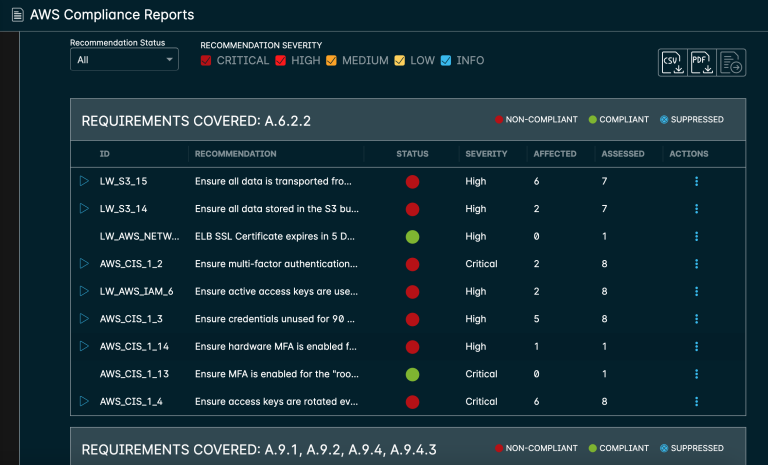
You can drill down further into each issue instantly seeing the affected devices or resources:
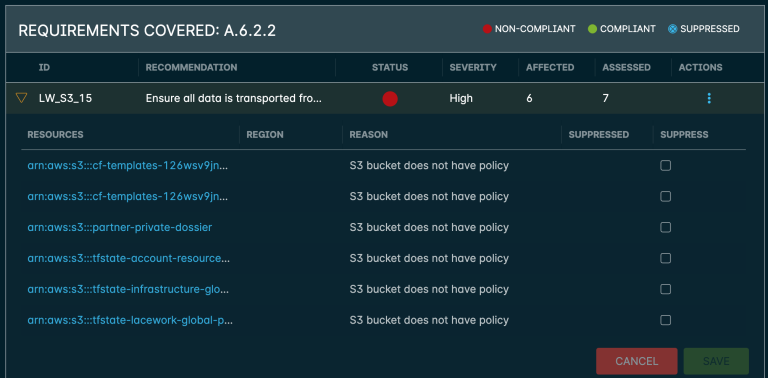
So it is essentially a snapshot of your Cloud Platform(s) within the two week period, the output of which is a report identifying every relevant vulnerability for your organisation type that arms you with the knowledge of identification of legacy issues, current build script issues and unknowns.
The report itself includes links to the actual remediation steps of each identified issue:
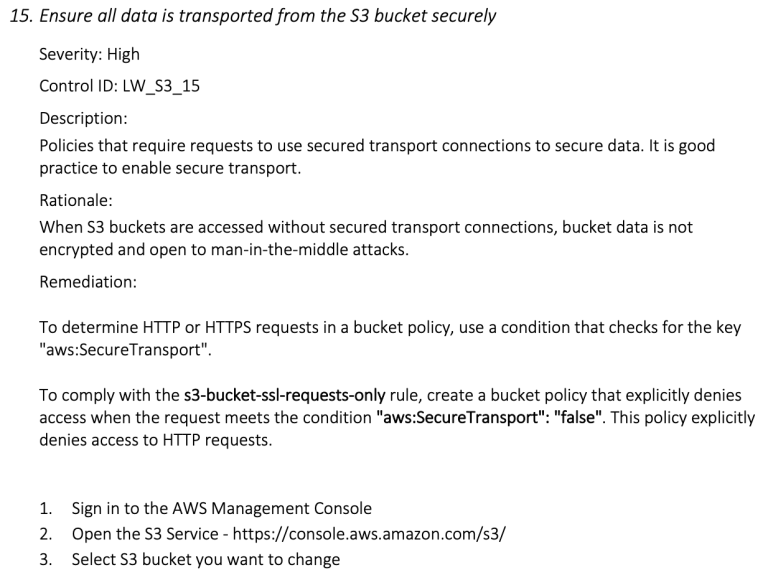
So it is not just bringing you a problem to solve, it is also bringing you the solutions.
For me, most products I have dealt with that offer Cloud Security Posture Management as a feature, want you to buy it first before you see the value but with the Cloud Security Assessment offering from Lacework I would encourage everyone to undertake it regardless.
The output is so valuable both from a viability and remediation perspective that I don’t foresee a single organisation not benefiting from the offer regardless of the outcome.
Think back to how it helped me in the example above, I was using a simple dev estate with minimal devices. How many resources do you have? How many Cloud Providers do you use? What do you need to comply with? When did you last audit your IaaS infrastructure? How would you even do so at Enterprise level? Would you then have to research the fixes for anything found?
With the Lacework Cloud Security Assessment, all of this could be done for you, and an extremely valuable report is provided as the output of the session. It takes minimal work to integrate Lacework with any Cloud Provider and then you just wait for the output.
“It has to be stressed that Lacework is not a CSPM and is only a small part of what the solution offers but if it was me, I would take advantage of getting this report even just for curiosity’s sake.”
More Resources like this one:
Lacework Cloud Security Assessment (CSA) Demo
Automating Security Assessments with Lacework
Automating Security Assessments with Lacework







