
Use Cases for Email Security with Varonis
Author: Beth Laws
Release Date: 11/06/2025
Every company and almost all employees use emails day-in day-out and the majority of email inboxes can often be a hidden home for a massive amount of sensitive data. If an email account were to be compromised, it could be used to exfiltrate any of this sensitive data. Not to mention, it could be used to impersonate employees or even conduct social engineering, which could jeopardise the whole network.
Despite these risks, data within emails and monitoring all this data and email activity can often be forgotten about by many organisations, enabling more and more cyberattacks to begin via email. Cyber criminals are savvy to this, and are aware many companies overlook email security, which is why a good data security solution should not forget about emails and should provide visibility on email sensitivity levels and detect unusual email actions on that sensitive data to prevent data exfiltration.
If an email account is compromised, it can be used to steal sensitive data, impersonate employees and conduct social engineering, which could jeopardise the whole network.
What can Varonis for Exchange Online do?
A good Data Security Posture Management (DSPM) tool should provide visibility on where sensitive data is stored, who has access, how it is being used and help to improve the security stance of these data stores. Varonis is a DSPM solution, so it goes further than preventing spam messages, or blocking malicious emails like some traditional email security tools. It helps by identifying sensitive data in emails to remediate any sensitive data over-exposure, improves your email security posture to prevent attacks and detects abnormal email activity in real-time.
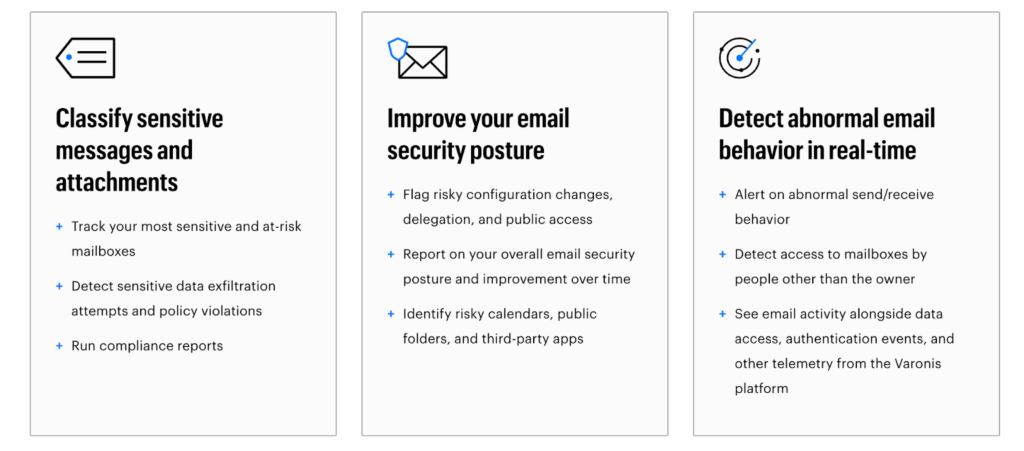
Detect and Classify Sensitive Data
The Varonis Data Classification technology uses patterns, dictionaries and key word matching along with proximity sensing to identify files that contain sensitive data that are of interest to your organization. This technology has now been extended to scan Exchange Online, looking across data within personal emails, shared inboxes, attachments and calendars. The classification technology has built in rules to scan and detect sensitive data, looking for things like credit card data, account credentials and personal information within your environment, but it’s also possible to add custom detection rules too to fit any specific business requirements such as detecting secret company project names, etc.
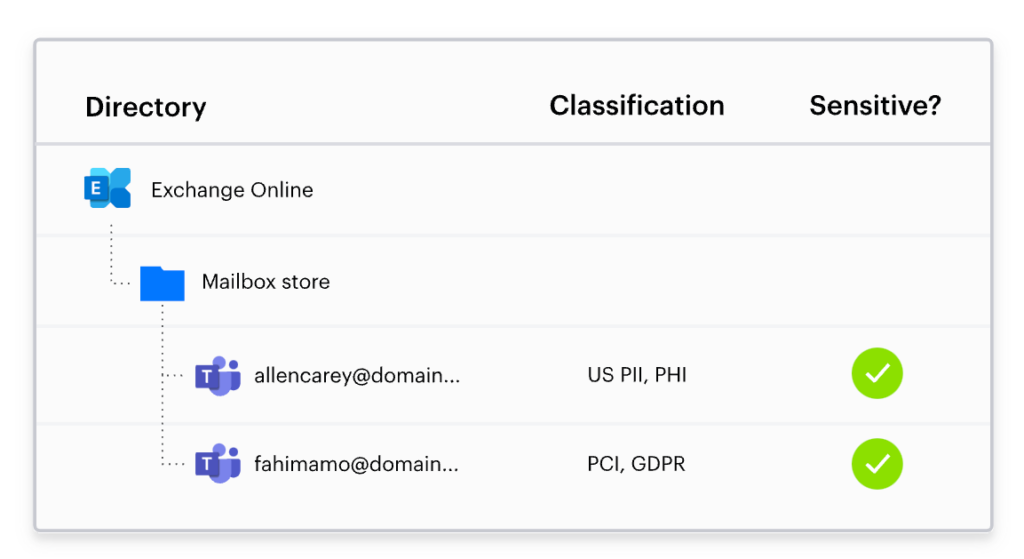
Flagging sensitive data within emails can also help to ensure businesses are compliant with their regulatory requirements. Varonis has an extensive library covering regulations, helping Compliance Officers to know which data may be subject to compliance standards such as GDPR or HIPAA.
Email Activity and Detecting Threats
Varonis has a built-in library of threat models which work alongside User Behavior Analytics, helping to detect insider and external threats within email. User activity across the environment is monitored continuously, so Varonis can understand what is normal behaviour for users and accounts, hence being able to alert on any unusual activity. In addition, the threat models detect more obvious suspicious activity, alerting on things such as malicious attachments in emails, strange-looking permission changes and automatic email forwarding.
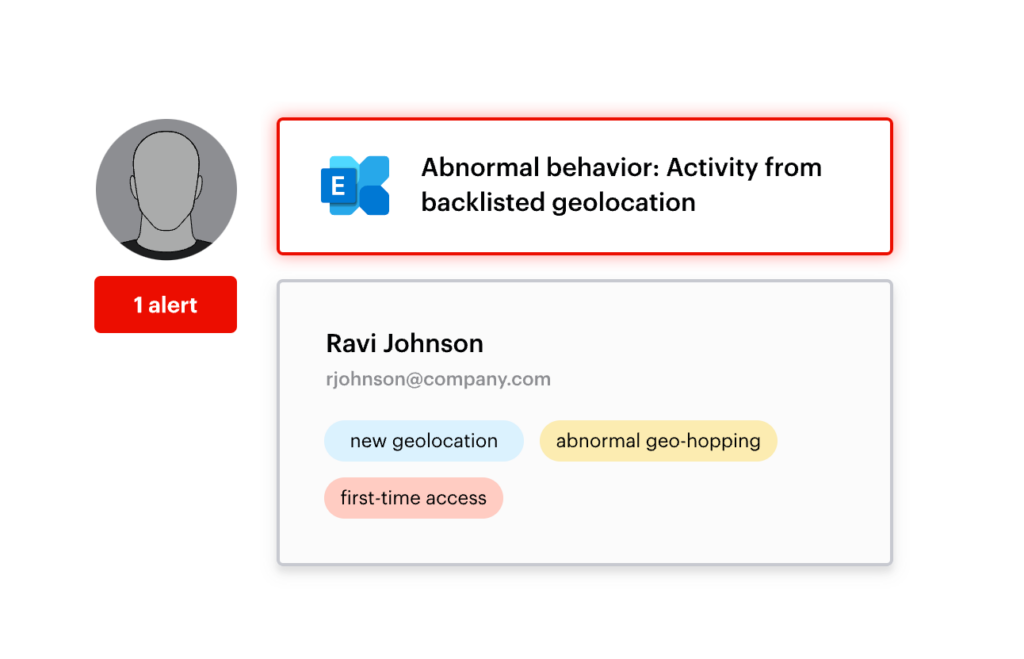
Investigating any alerts can be done within Varonis from the Alerts dashboard. You can drill down into the information behind the alert and gain more insights into the story behind it. Varonis can show an audit trail of all email activity, as well as monitoring events from Active Directory, Entra ID and M365, helping security teams to investigate and understand a user's activity more thoroughly.
Email Security Dashboard
Varonis Saas comes with an Exchange Online Dashboard which displays crucial high-level insights on what sensitive data resides within email. From here, you can instantly find useful information such as, what type of sensitive records reside within Exchange Online, what sensitive data is shared externally or exactly how many sensitive messages are in your environment.
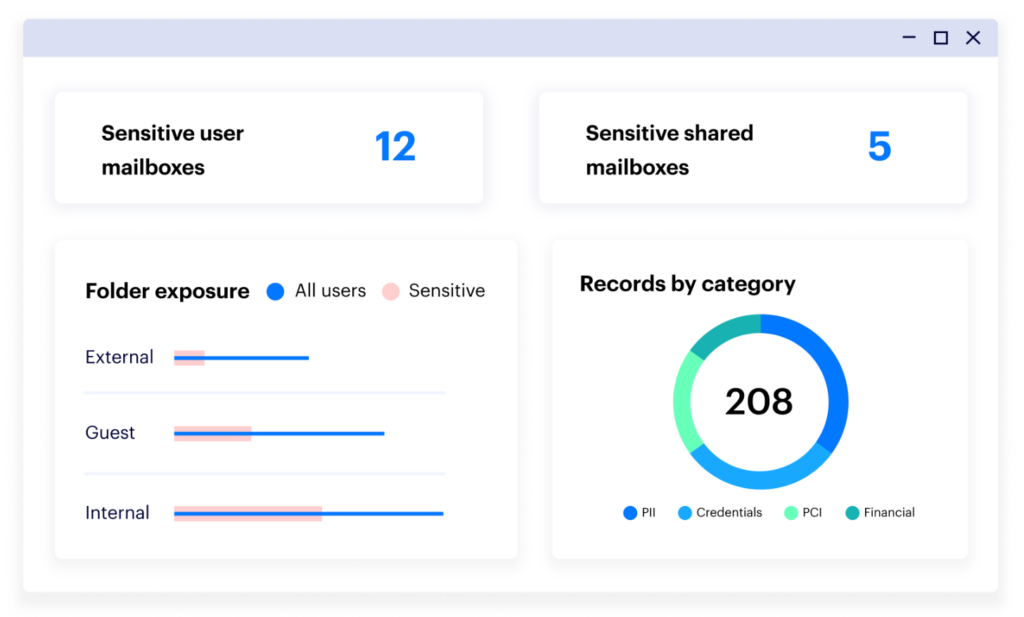
From the dashboard widgets, it’s easy to click and dive deeper to gain more context on your sensitive data. For example, clicking on the Number of Sensitive Messages panel then provides you with more information on those exact emails, showing you details of the subject of the mail, sender and recipient information and exactly what type of sensitive data is in there.
No business should settle for a DSPM solution which doesn’t monitor and protect email storage. Varonis identifies the most sensitive mailboxes and calendars as well as monitoring email activity and detects email-based attacks. If Varonis may be of interest to you and your company, check out our Varonis Partner Page for more information.

