Varonis SaaS Platform Overview (2025)
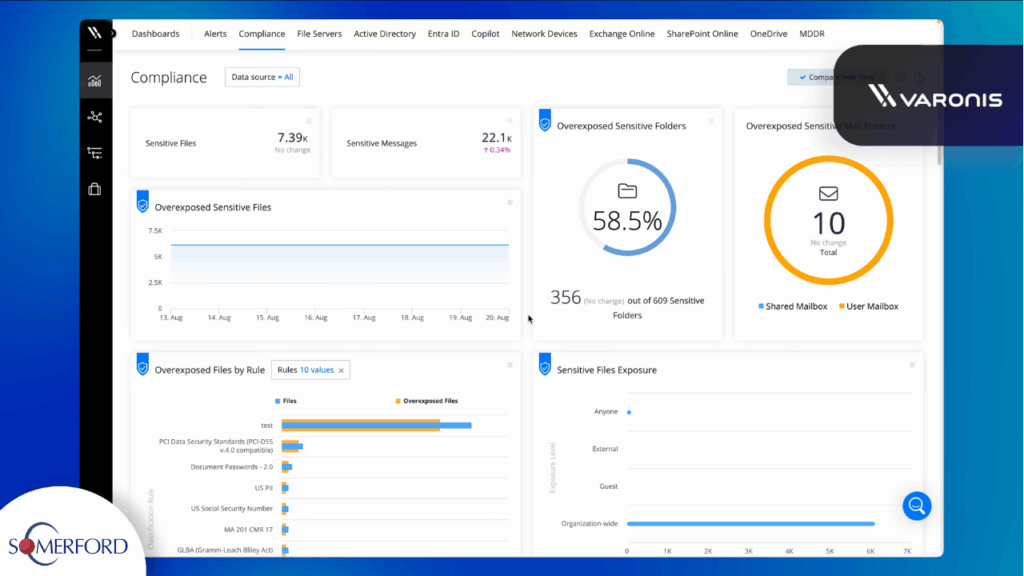
Video Varonis SaaS Platform Overview (2025) Series Overview Explore the Varonis SaaS Platform In this demonstration, Beth Laws, Varonis Consultant at Somerford Associates, walks through the key features of the Varonis SaaS platform and how it helps organisations strengthen data security, maintain compliance, and detect threats. The session covers how Varonis provides visibility across Microsoft […]
Varonis SaaS Platform Overview (2025) Read More »