
Setting up SplunkWeb with Third Party Certificates End-to-End on a Built Environment (Part 3)
Author: Laurence Everitt
Release Date: 29/05/2024
Introduction
This is the last part of a 3 part explanation of how to uplift SplunkWeb from presenting a regular HTTP website to using full-blown SSL/TLS HTTPS website, end-to-end. For further information, please see the previous parts, Part 1: Overview and Part 2: The Details.
How to Read the Contents of an X509 Certificate with OpenSSL
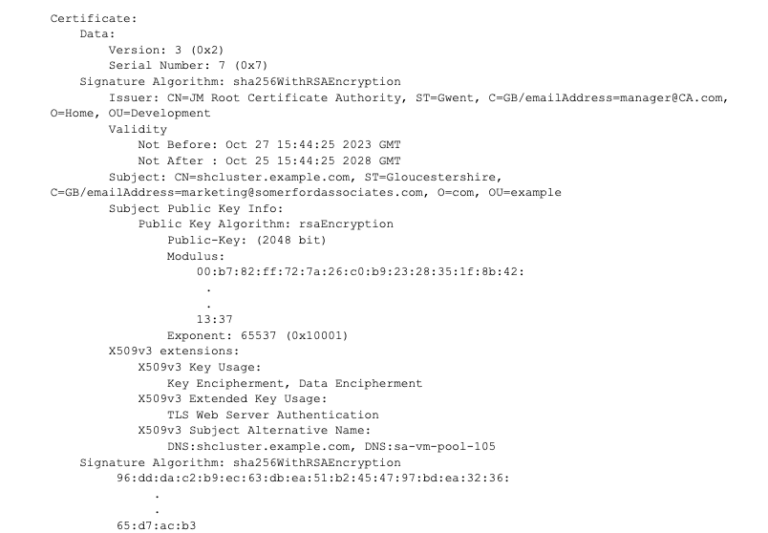
If you don’t know what the certificate contains, use this command to read the contents of the cert.pem:
Also in this Blog Series...

This should respond with the human-readable contents of the certificate such as this:
How To Verify The Certificate Chain With Openssl
Try this command to verify that the certificate.pem is valid from the certificate-chain.pem CA File:

This should respond with the following if all is okay:
How to Verify that the x509 Certificate Matches the RSA Key with Openssl
In this case, you use two commands - one upon the certificate and one on the key, asking for the modulus of the item. These two items then need to be compared and found to be IDENTICAL:

If the certificates match, you will get the following, otherwise they will differ:

How to Verify that the Certificate Period is Valid with Openssl
Use this command to verify the dates that the certificate is valid for the manager.pem:
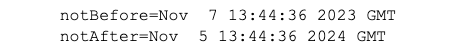
This should respond with something like the following message. Make sure that this time includes the current date:
Links Used in this Article:
https://docs.splunk.com/Documentation/Splunk/9.1.2/Deploy/Manageyourdeployment
https://smallstep.com/blog/if-openssl-were-a-gui/
https://learn.microsoft.com/en-us/skype-sdk/sdn/articles/installing-the-trusted-root-certificate
https://www.redhat.com/sysadmin/configure-ca-trust-list
https://www.ssl2buy.com/wiki/root-vs-intermediate-certificates
https://www.xolphin.com/support/Certificate_conversions/Convert_pfx_file_to_pem_file
https://knowledge.digicert.com/solution/how-to-convert-a-certificate-into-the-appropriate-format
https://en.wikipedia.org/wiki/PKCS_12#
https://docs.splunk.com/Documentation/Splunk/9.1.2/Security/SecureSplunkWebusingasignedcertificate
https://docs.splunk.com/Documentation/Splunk/9.1.2/Security/HowtoprepareyoursignedcertificatesforSplunk
https://acquia.my.site.com/s/article/360004119234-Verifying-the-validity-of-an-SSL-certificate







