Configuring Data Loss Prevention for Your
Web Traffic When Using Netskope
Release Date: 09/08/2022
In this blog we are going to be looking at just how easy it is to configure Data Loss Prevention, content aware policies on your web traffic when using Netskope.
The machine I am currently on is a server sitting in AWS and has a Netskope client installed on it, this in turn is steering all of my web traffic to a Netskop tenant that is in the Cloud.
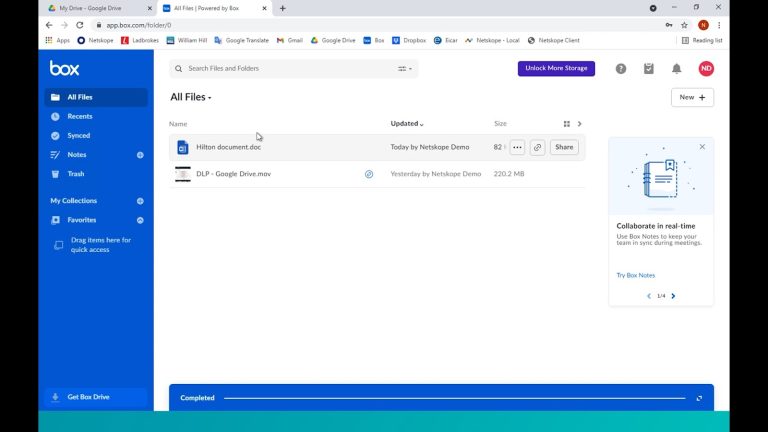
Let’s pretend we are a Google house, we use Google Drive and within this, we have a number of files that contain GDPR info.

As a use case, let’s pretend this Hilton Document contains the personal information of a staff member and we urgently need it to be sent to a 3rd party to confirm a booking.
The 3rd party however is having issues with accessing this via Google Drive and for some unknown reason email is blocking it.
So, the employee in this instance, registers for one of many free cloud storage apps, in this case Box, using their employee credentials too.
They then upload the file to this unsanctioned app, they share it with the 3rd party and all is well.
Is it though, as in this example they not only opened themselves up to further risk by using their work credentials to register for the app but they have also essentially breached multiple GDPR policies as the file is now outwith control of the company, they have no visibility of it, etc.
So how can we close such data exfiltration points with Netskope?
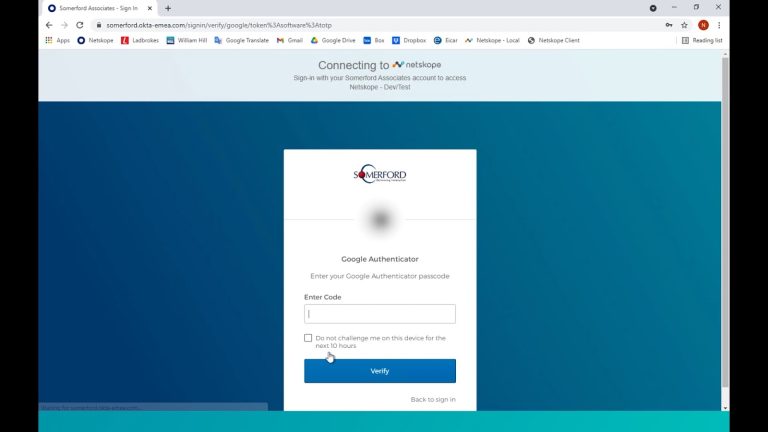
Let’s start by logging into our Netskope cloud portal, as always we are using Okta to centralise user management of the tenant and provide us with MFA as should be standard with any public facing login page like this.
In our policies page, we could go the Secure Web Gateway or CASB route and completely block every single unsanctioned cloud storage app outright or by way of the risky activities that the user may perform when accessing such apps or sites. In this example, we are creating a policy that is going to block uploading, posting, editing or creating any file that exists in a cloud storage app or site.
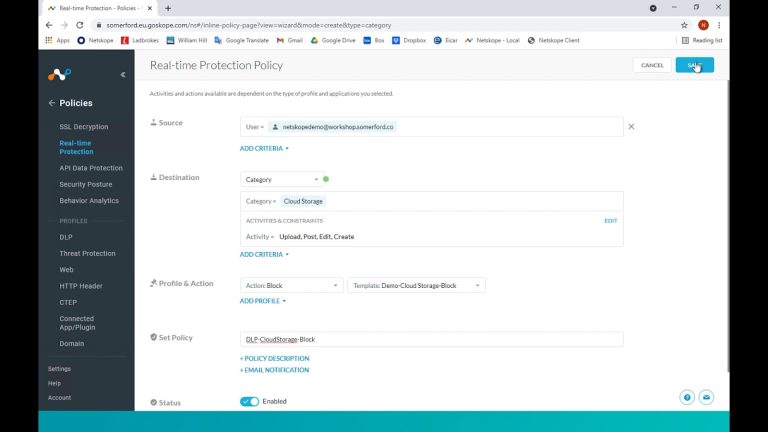
As we are a Google house, we would then need a counter acting policy that allows these things within Google Drive.
This is not ideal though as it may negatively impact how we interact with customers or suppliers who rely on other 3rd party Cloud Storage apps, so it is too strict a policy for us to limit these activities.
Instead, we want to enact our policy based upon content and in this example, based on GDPR content.
So instead of a web access or cloud app policy, we want to create a DLP policy.
As previously, we want a policy to block the movement of GDPR to unsanctioned cloud apps so we choose cloud storage as our category, but with the DLP policy option we get to choose a profile for what Netskope is to check against. For this we are going to choose the out of the box GDPR profile.
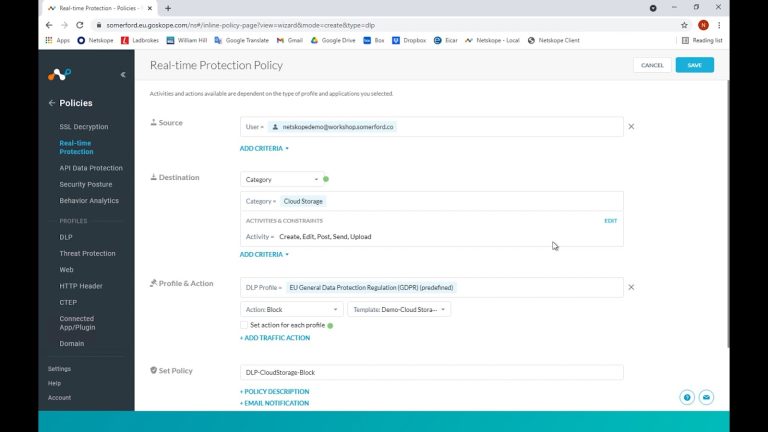
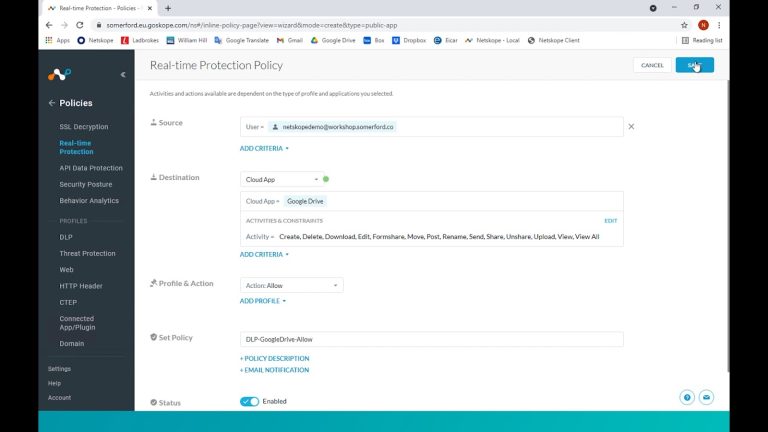
We again in turn have to create a counter policy for Google Drive since we class this as sanctioned and trust it to contain GDPR info that users are allowed to download.
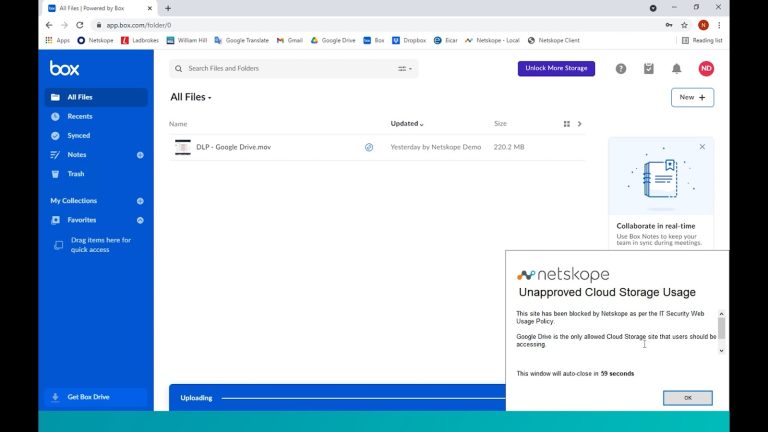
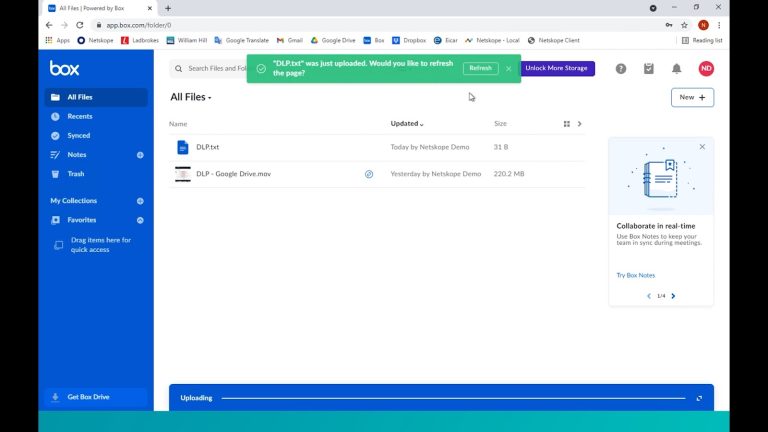
With our DLP policies in place, we return to Box and try to upload our document that contains GDPR info and you can see that this is blocked. Netskope has read the document, has identified it contains GDPR information and it has stopped the user in their tracks from uploading it.
To demonstrate this further, lets create a file that contains no GDPR information and try to upload this, as can be seen this works hence Netskope is checking the content of these files in realtime and taking action based upon our real time content aware DLP policy.
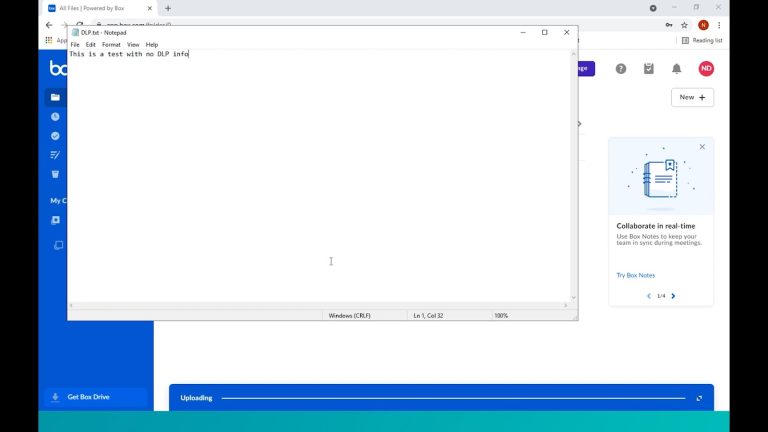
This is all well and good when it comes to text based documents so let’s take it a little further by asking Netskope to inspect an image based upon their Advanced DLP offering.
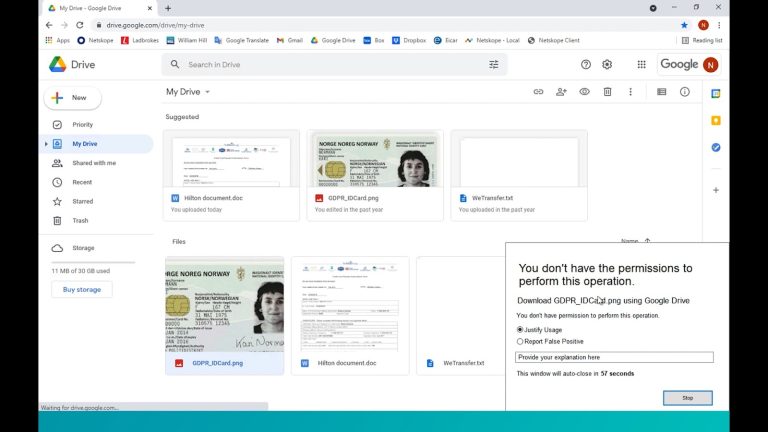
In Google Drive, we have a mock ID card that contains GDPR info but this is an image, it is not contained in a text based form.
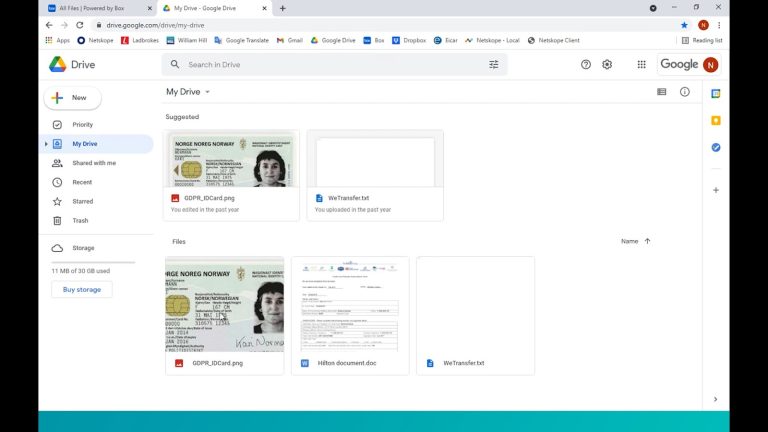
With the policy we just created, Netskope will allow me to download this and upload it to Box as with our current configuration of the policies, it is only looking at text based documents.
Therefore, in Netskope, we are going to create a policy that will inspect images for identifying information.
I have previously created what is known as a fingerprint of the ID card in question and I have created a DLP profile within Netskope telling it that should Netskope see the same kind of image (with an 85% match threshold) then I want it to use it’s Optical Character Recognition style technology to read the image and take action if there is a match and block this from being downloaded from Google Drive.
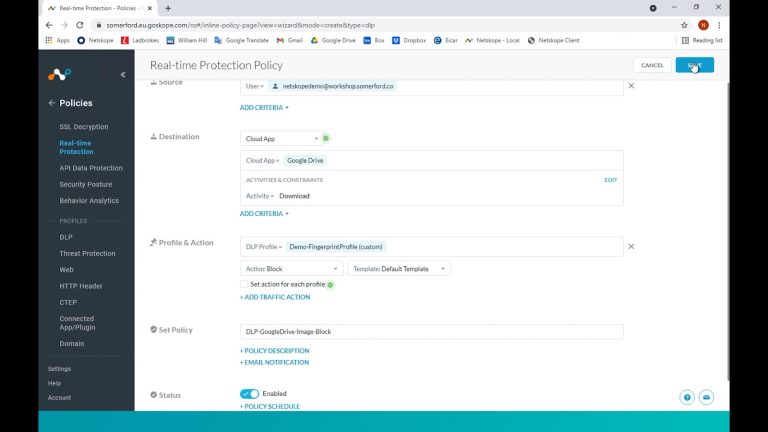
When the policy is saved and synchronised, we return to Google Drive, try to download the image, and we are blocked.
If you wish to know more about Netskope and how it can assist your organisation in today’s SASE and Cloud based world then please get in touch with us via our contact form near the bottom of this page!
More Resources like this one:
Somerford's Added Value Explained
Partner & Customer Testimonials |
Business Value Panel Discussion
Netskope Explained: Series Summary
Netskope Smart Cloud Security 101—
Short Use Cases & Tutorials
Get in Touch
Contact one of our pre-sales team through our contact form.