Stronger Together: SecurityScorecard and Splunk
Author: Andrew Weston – Security Consultant
Release Date: 04/04/2019
Splunk Customers can now utilise SecurityScorecard’s certified app to improve 3rd party risk intelligence as well as gaining insights into their own cybersecurity risk. The SecurityScorecard application is now available on Splunkbase.
Integrating SecurityScorecard security ratings and findings into Splunk solutions enables deeper insights into enterprise and 3rd party cyber risk. The combination of SecurityScorecard security ratings, generated from externally observable data, and Splunk’s AI and machine-learning capabilities facilitates more informed decisions, 3rd party risk program scalability, and automated response to cybersecurity risk events. This fully integrated solution enables customers to gain comprehensive visibility into their vendor ecosystem risk directly from the SIEM.
What does the SecurityScorecard App for Splunk do?
It will offer customers the ability to monitor three components:
- SecurityScorecard’s overall letter-grade security ratings, which give customers the ability to quickly and easily understand the cybersecurity posture of an organisation via an easy-to-understand A-F rating scale
- SecurityScorecard’s underlying factor data in key risk categories, including Application Security, Malware, Patching Cadence, Network Security, Hacker Chatter, Social Engineering, and Passwords Exposed. Each of these factors is predictive. For example, companies with a C, D, or F rating are more than 5.4 times more likely to experience a data breach than those with an A or B rating.
- SecurityScorecard issue-related data, which offers a breadth and depth of critical data points across 87 different issue types not available from any other security ratings provider.
You can choose to monitor your own scorecard or 3rd party scorecards or both. Once the app is installed, the app will begin pulling scores and issue level event information on a daily basis into Splunk. You can then leverage the power of Splunk to search, visualise and take action on the information that is logged, enabling you to efficiently monitor your own cybersecurity risk as well as the risk posed by your 3rd parties.
What can I do with the SecurityScorecard data?
Once SecurityScorecard data begins flowing into your Splunk instance, there are numerous applications you can use it for. Some examples include the ability to merge:
– SecurityScorecard data with other in-house or 3rd party threat intelligence data you may have
– Internal cyber security event and log data with SecurityScorecard ratings and issue level event information (e.g. combine your firewall log data with network security findings from SecurityScorecard).
Additionally, you can:
– Monitor changes in overall & factor level scores on your own or 3rd party scorecards
– Monitor new issues being added, removed or resolved on your own or 3rd party scorecards
– Leverage SecurityScorecard data in existing vendor risk management or other security operations programs being run out of customer SIEM platforms directly
– Monitor for new threats, adverse score events, self-assessment score etc.
You can also leverage the power of Splunk’s visualisation features to create dashboard with SecurityScorecard data included. Below are some examples of the type of dashboards you can build to monitor for changes in scores and issue level events
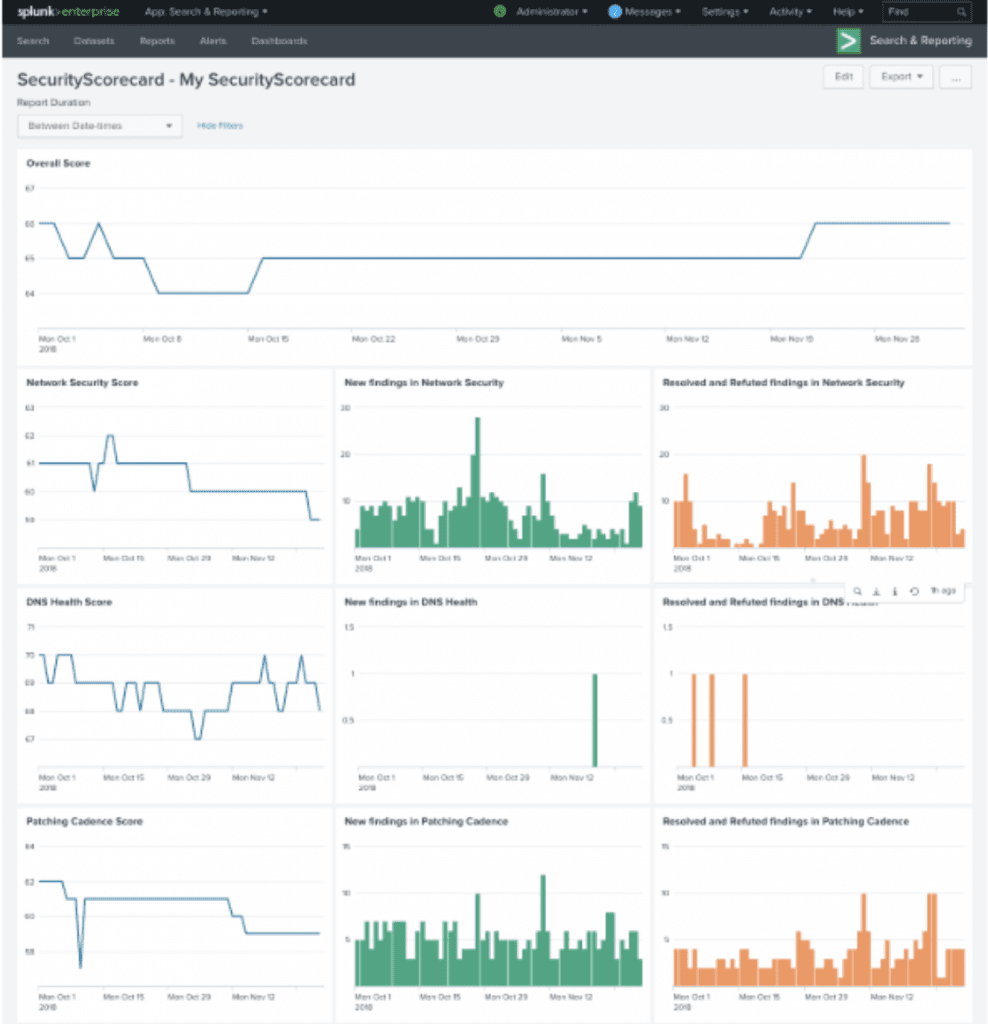
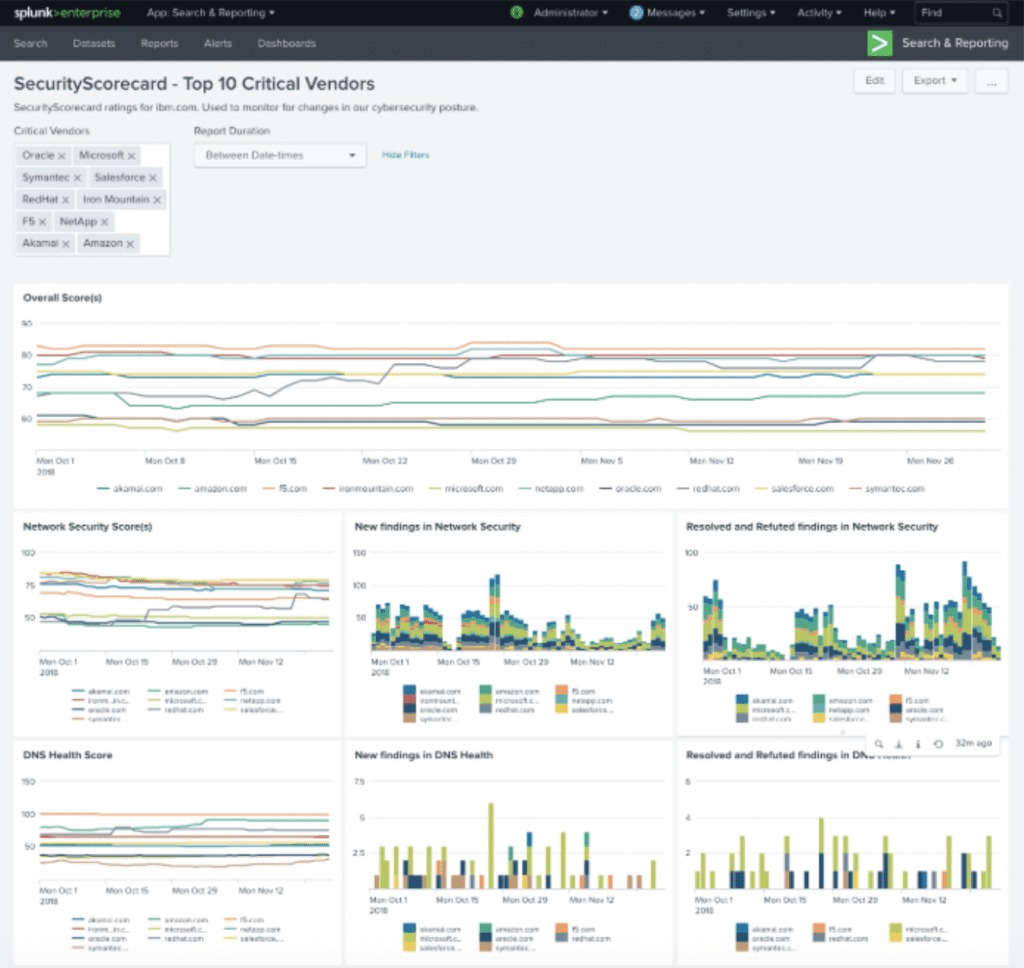
How does the app fetch data and how often does it get new data?
The SecurityScorecard Splunk app leverages the SecurityScorecard API to retrieve scores and issue level findings information, this is why the app requires an API key as part of the setup process. The SecurityScorecard Splunk app gets fresh data every 24 hours.
When the SecurityScorecard Splunk app runs, it will retrieve the following data points:
– List of companies in any monitored portfolios
– Overall score
– Factor Level score
– Changes in the Scorecard Event Log for the day
Does the app work on Splunk Cloud?
Version 1.3 currently supports Splunk Enterprise but there are plans to add support for Splunk Cloud in an upcoming release.
How do I search for data?
Splunk allows users to search for data by leveraging Search Processing language (or SPL). Once the SecurityScorecard app starts logging data to your Splunk instance, you can leverage SPL to query for the data. Below are a couple of examples to help you get started.
Example Queries
1. Query for all data logged by SecurityScorecard
To query for all data logged by SecurityScorecard you can simply type in sourcetype=SecurityScorecard into the search bar. This query will return all events logged by the SecurityScorecard app.
2. Query for all data logged by SecurityScorecard at the overall score level
To query for all scores logged at the overall level you can enter the following query: sourcetype=SecurityScorecard cat=Overall into the search bar. Additionally, if you want to filter to a specific domain you can do that by adding a domain to the search criteria like this sourcetype=SecurityScorecard cat=Overall domain=securityscorecard.com
3. Query for all data logged by SecurityScorecard at the factor score and issue level
You can query all factor level data by specifying Factor as the category sourcetype=SecurityScorecard cat=Factor and similarly you can query for all issue level data by specifying Issue as the category sourcetype=SecurityScorecard cat=Issue
4. Query for all data logged by SecurityScorecard for a specific domain
If you want to filter on a specific company you can do that by specifying the domain in the query sourcetype=SecurityScorecard cat=Overall domain=ibm.com
Join us at a later date for our next blog on SecurityScorecard Atlas, the leading questionnaire and evidence exchange platform.
More Resources like this one:
How Varonis & SecurityScorecard Support Telecoms Organisations in Improving Security | Introduction
Security Ratings Demystified
Get in Touch
Contact Beth or the rest of our pre-sales team through our contact form.