Getting Started with Risk Based Alerting (RBA Part 1)
Author: Ben Marrable
Release Date: 02/02/2022
Perhaps you’ve seen the videos from Splunk .conf by Jim Apger and co. Perhaps you’ve come completely new to this blog and have no idea what RBA means, well let me explain…
Relevant Blog Post:
RBA is the concept of alerting from a risk based approach. Where we take it further is by incorporating Cyber Defence Frameworks such as the Lockheed Martin Cyber Kill Chain or the MITRE ATT&CK Matrix to provide additional context to the alert.
So, How does it work?
- By Leveraging Splunk Enterprise Security’s Risk Framework
- And Dynamically calculating a risk score for each alert by applying risk modifiers.
Risk modifiers can be anything from:
- The Entity’s priority (Asset, Identity or other)
- The Entity’s Category (contractor, cardholder, privileged etc.)
- Whether the User is an Administrator
- Whether the Entity involved is on a watchlist
- The Time of Day
- The Location of the Event
- Anything else you can think of that would be relevant
What do you need to start with?
- Accurate Asset and Identity Lists in Enterprise Security (see my blogs on assets and identities here)
- Splunk Enterprise Security v6.4+
- A desire for higher fidelity alerts in your SOC
How does it all fit together?
The first thing to do is identify which use cases are to be a part of an RBA model, these could come from your own in house user stories, ones derived from Splunk Security Essentials, ES Content Update or ones mapped to your limited coverage areas in the MITRE ATT&CK Matrix or Cyber Kill Chain.
Once you have your list of use cases and have derived the required detection searches for them. The next step is to add them into Splunk Enterprise Security as Correlation Searches. However instead of using the Notable Event adaptive response action, we are going to only add risk as the adaptive response. Correlation Searches of this type are known as Risk Rules or RR for short. It makes sense to prepend the title of the search with “RR – ”, so as to distinguish them from regular correlation searches.
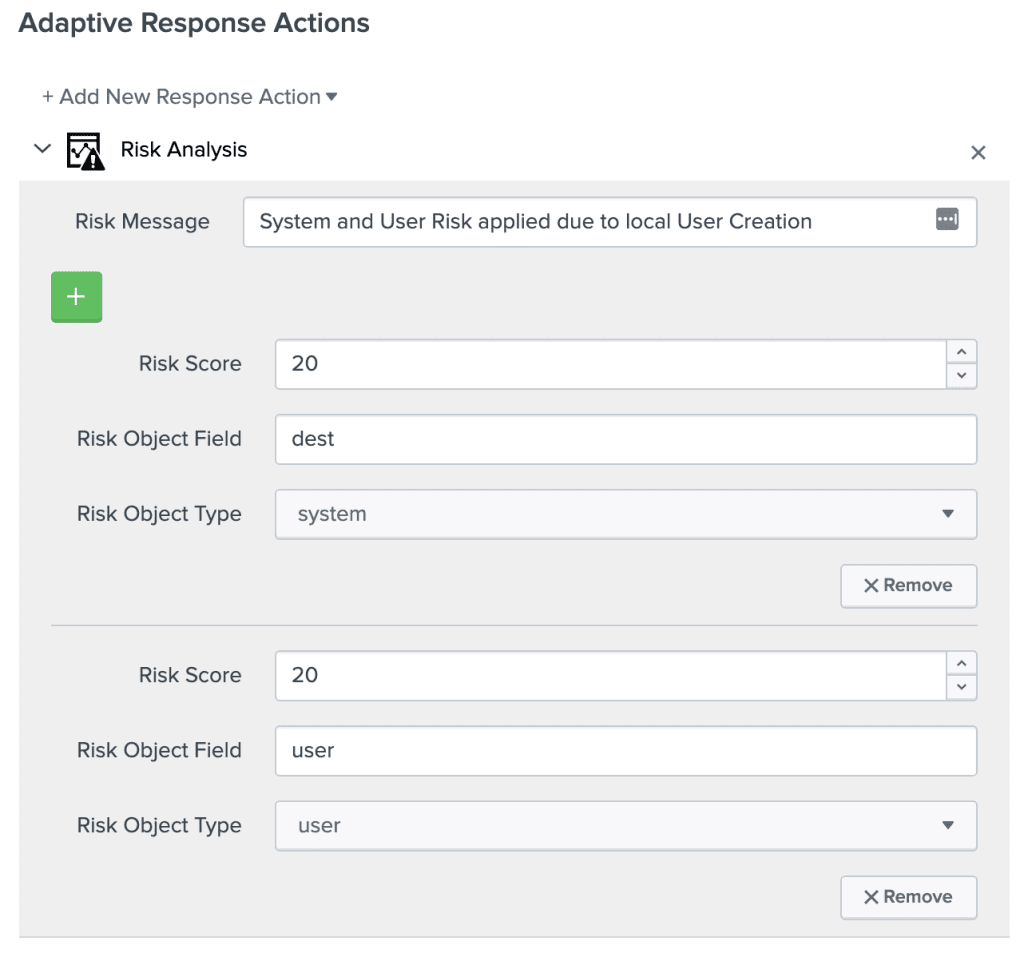
How much risk should you apply?
At a high level the risk should map to the severity or impact of the detected behaviour, but also take into account some confidence level that what you’ve detected is accurate. As a starting point, I would apply the following base risk scores, multiplied by the following confidence multiplier based on the percentage of expected true positives from the alert. These scores are aimed at an alerting threshold level of 100 points of risk, that level is of course completely tunable as we will discuss in the second blog in the series.
Severity:
- Informational (5)
- Low (25)
- Medium (50)
- High (75)
- Critical (100)
Confidence Percentage Multiplier:
- 0-10% (0.1)
- 11-20% (0.2)
- 21-40% (0.4)
- 41-60% (0.6)
- 61-80% (0.8)
- 81-100% (1)
Here’s a simple table to make that easier to understand.
Severity/Impact | Confidence | Risk Score |
|---|---|---|
Medium | 5% |
50 * 0.1 = 5 points of Risk
|
High | 33% | 75 * 0.4 = 30 points of Risk |
Critical | 75% | 100 * 0.8 = 80 points of Risk |
Once you have the base risk scores aligned, it is now time to setup your risk modifiers, these can be accessed by going to Splunk Enterprise Security -> Configure -> Risk Factor Editor
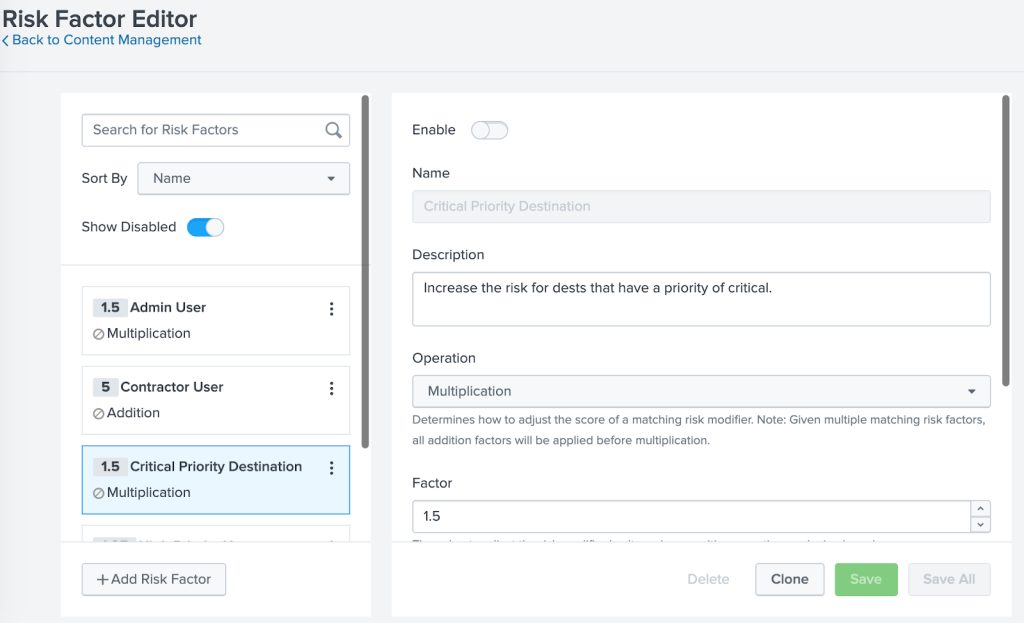
Enable any that you feel map to the risk rules appropriately that you have in place and then monitor their effects, I will go into more detail on this in my next blog on tuning concepts for RBA.
Finally, we should produce some alerts from all of this logic we’ve been building, this is where the term Risk Indicator Rule (RIR) comes in. A risk indicator rule is a logical search that produces alerts when a defined threshold of risk is reached over a set period of time AND/OR where a number of framework steps/phases/tactics are associated with an individual entity (i.e. detecting an indicative weaponization activity, an indicative delivery activity and an indicative command and control activity by a user account).
There are two that come out of the box with Splunk ES 6.4+, those are:
- RIR – 24 hour risk threshold exceeded
- RIR – 7 day ATT&CK Tactic threshold exceeded
The 24 hour rule has the following alert clause, meaning it will alert when there is at least 100 points of risk over a 24hr period.
| where risk_ScoreSum > 100 and risk_duration<86400
The 7 day ATT&CK Tactic has the following alert clause, meaning it will alert when there are at least 3 tactics over 4 different techniques within a 7 day period.
| where tacticCount >=3 and sourceCount >=4 and risk_duration < 604800
We will take a look at the full search in part 2 of the blog and indeed how and when to tune them.







