Configuring Threat
Protection on your Web
Traffic with Netskope
Author: Paul Graham
Release Date: 02/08/2022
In this blog we are going to talk about how easy it is to configure Threat protection on your web traffic when using Netskope.
The machine I am currently on is a server sitting in AWS and it has absolutely nothing in the way of Threat Protection outside of that which is native to Windows.
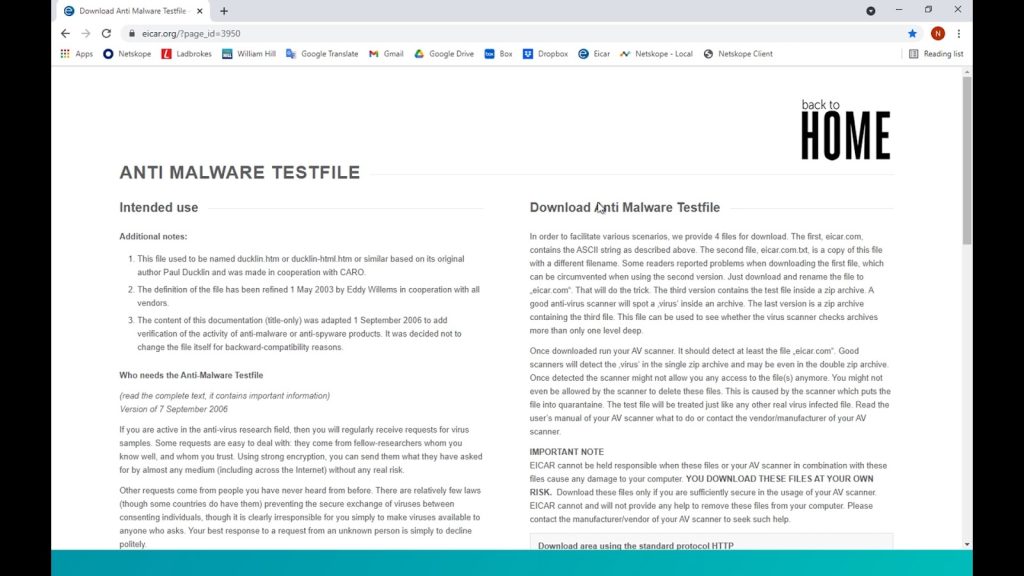
To demonstrate, lets go to EICAR and download their malware test file.
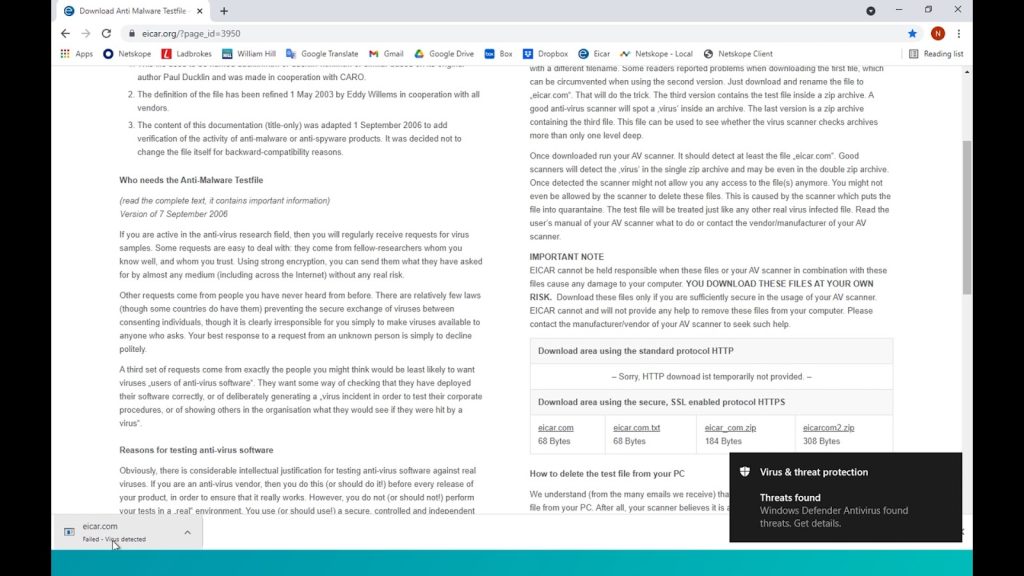
As can be seen, Windows doesn’t allow the download and tells us the file was infected.
We don’t want it to ever get this far though, we want to stop such a threat at its source as opposed to ever allowing it onto our machine for it to be scanned.
On this machine, we do however have a Netskope tenant installed and when enabled, we can see that it has been configured to steer all of our Web Traffic to our cloud tenant for inspection.
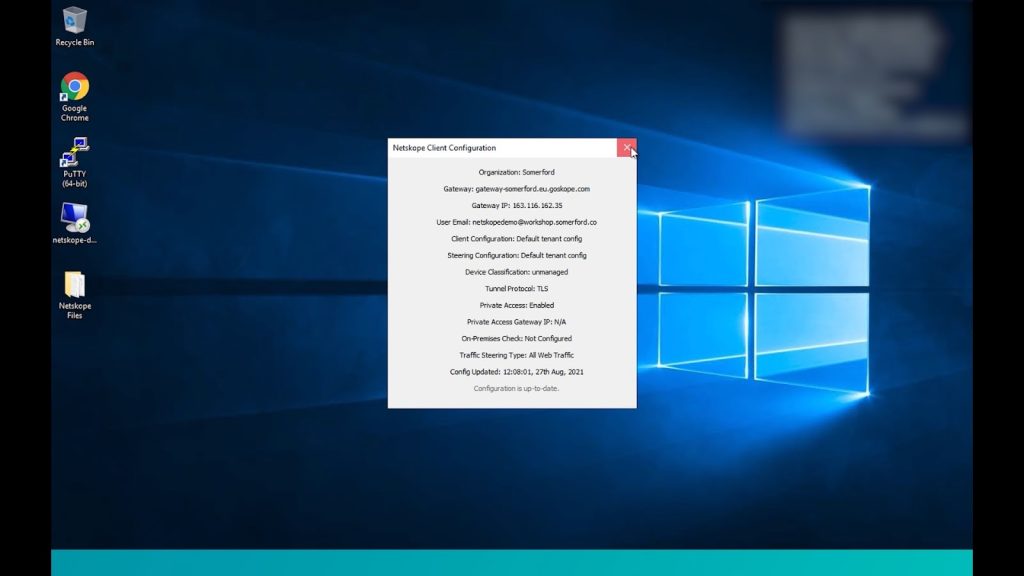
This is important as while most legacy Secure Web Gateways offer some level of threat protection, this is usually done by way of onsite appliances in data centers, our traffic in this instance would have to be on the company network before the protection was applied. When it comes to remote workers and cloud infrastructure, this can be problematic however as Netskope’s tenant is in the cloud, we have protection no matter where we are located.
There are no policies applied within this tenant yet so here we log into the Netskope Cloud Tenant directly. As always, since it is a public facing cloud portal, we want to have extra security such as MFA with Okta in this instance.
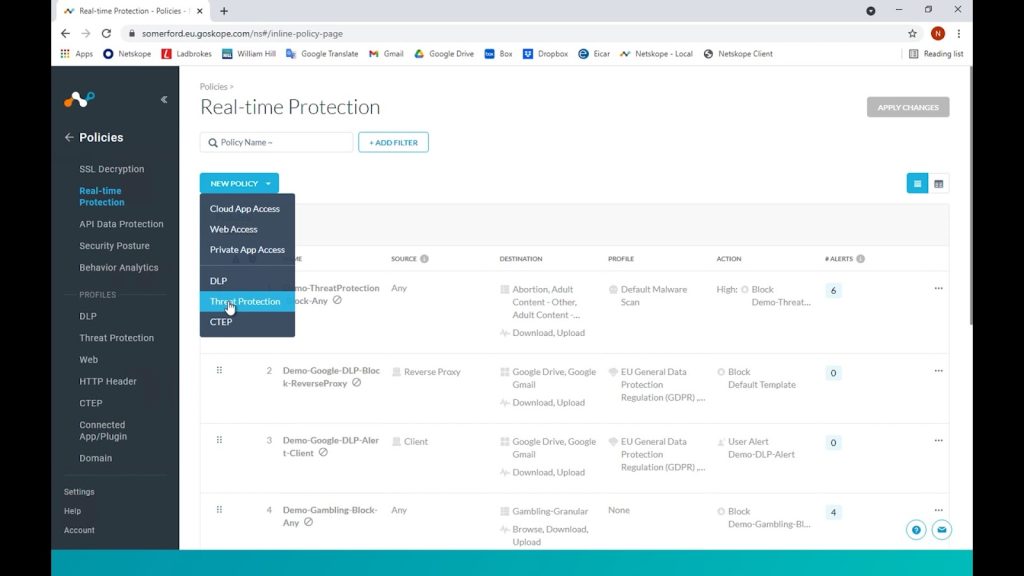
Once logged in, we choose Real Time Protection and we want to create a new Threat Protection Policy.
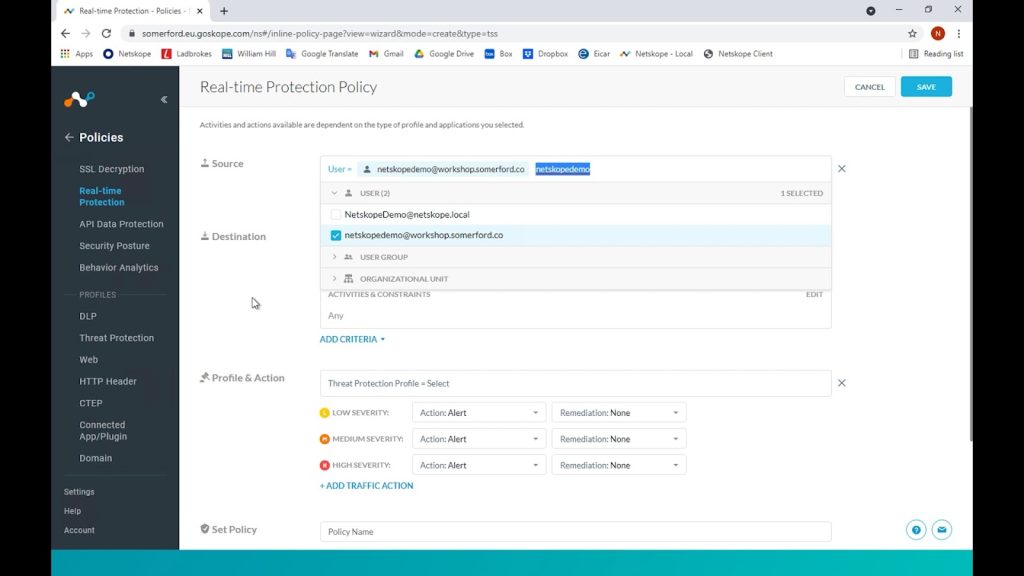
We can apply this policy to individual users or adopt a more role based approach by choosing groups or organisational units, in this instance we will apply ours to an individual user.
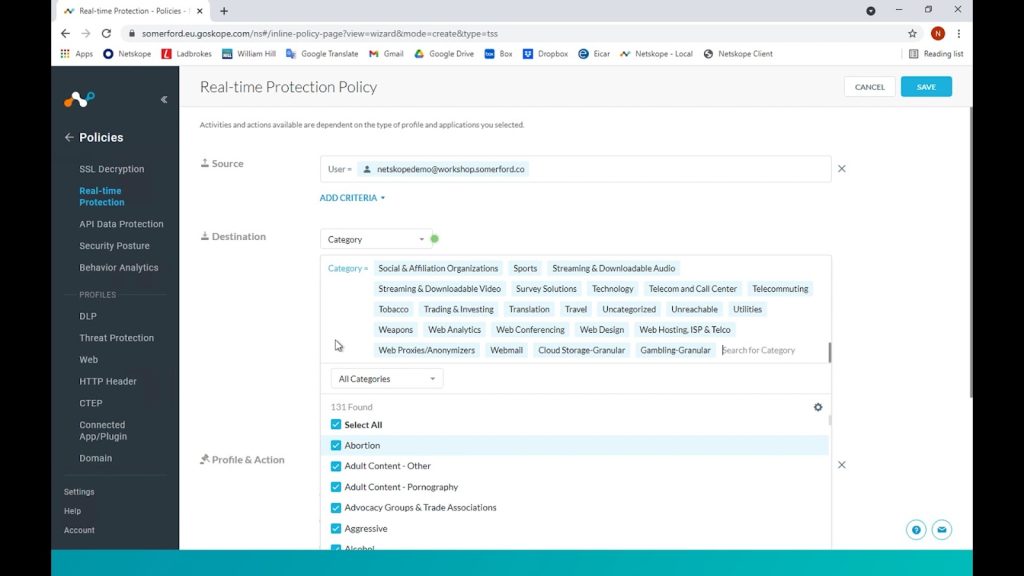
For our destination, we can granularly apply the policy to Cloud Apps and categories but since it is such an important policy, we want it to be applied to every category of web traffic.
We can choose granular activities too but in this case, we want all uploads and downloads to be checked for threats.
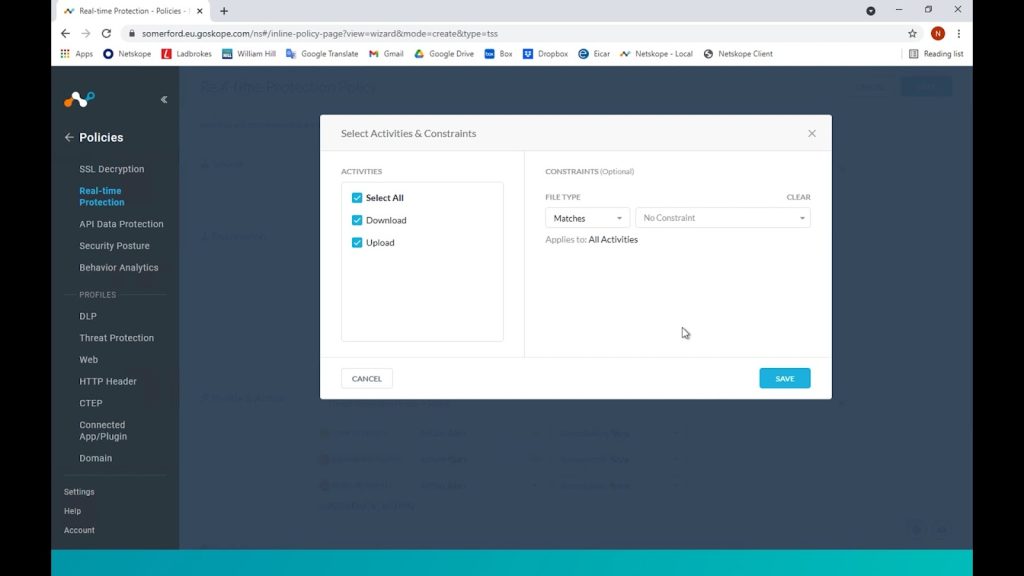
We don’t have any other threat protection profiles configured so we will choose the default Netskope one here that should be noted is updated constantly as new emerging threats are discovered.
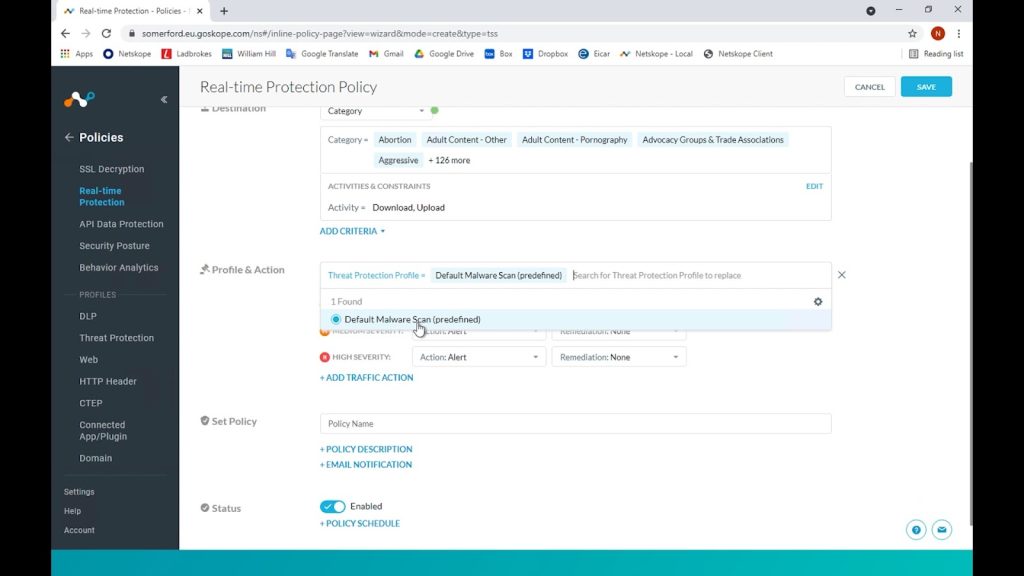
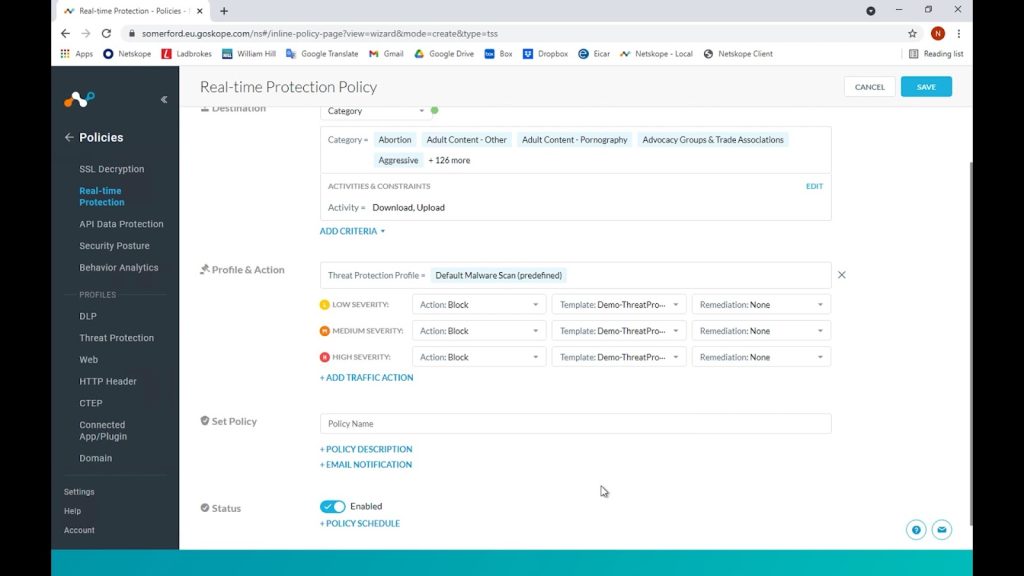
We can configure different granular controls based on perceived threat severity but in this instance we will choose to block for all.
We have also previously created a custom user notification template to better educate our end users for this type of block so we also choose this in our policy.
Lastly, Netskope can be integrated with tools such as Crowdstrike wherein remediation actions can be specified however, this dev tenant does not have this configured so we will leave these options as none.
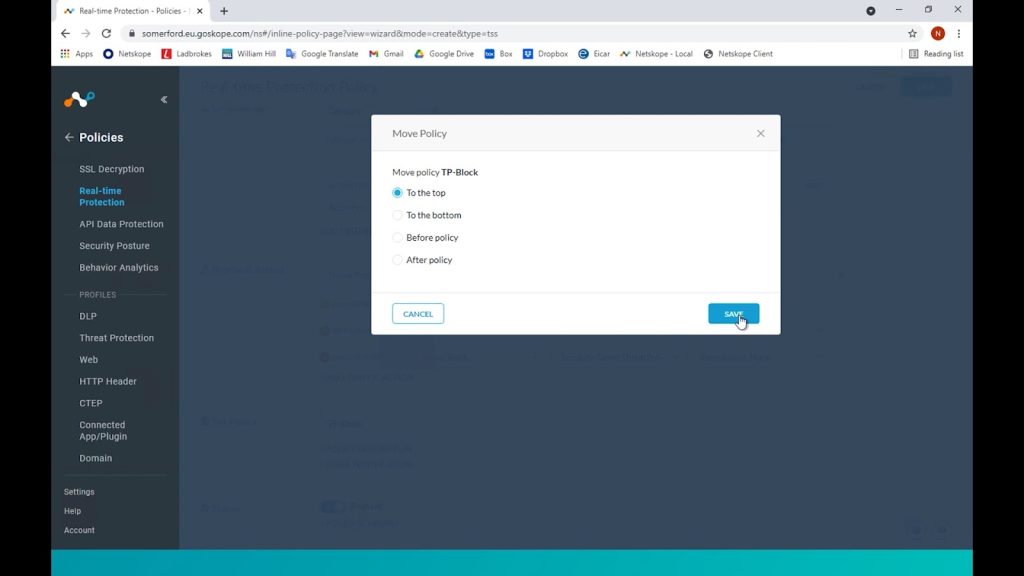
As it is such a critical policy, we want this to be at the very top of the list and then our policy is synced and enacted on all of our end user’s traffic.
Now if we return to the EICAR site shown previously and attempt to download the same malware file as before, we are blocked from doing so, the Netskope cloud tenant has inspected the file, has detected malware contained therein, has blocked us from downloading it and has clearly advised as to what has just happened.
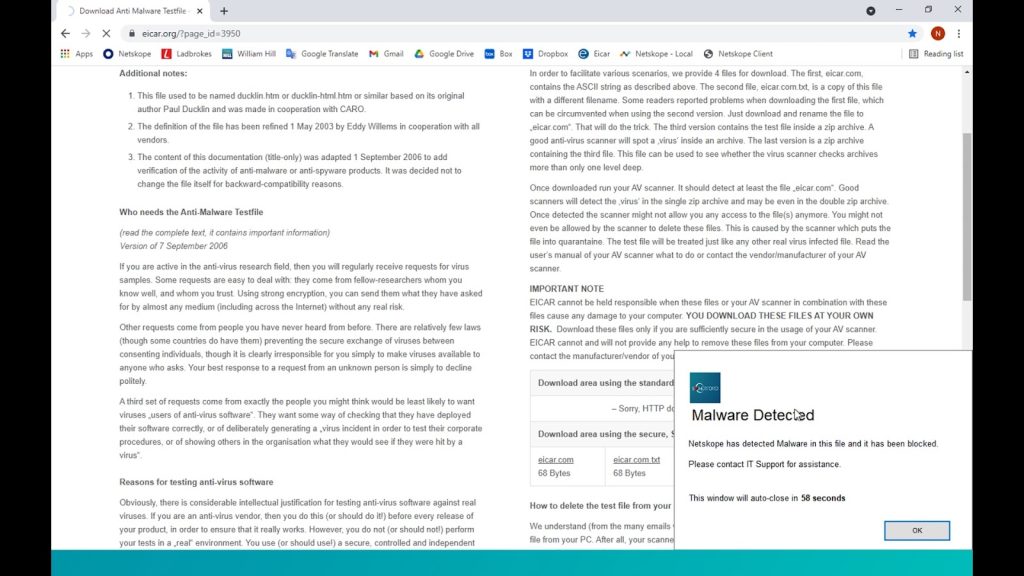
The file has never reached our machine and has been stopped at source, in real time, and we have not had to be on the company network for this to happen hence no matter where in the world we are working from, we now have real time web based threat protection.
If you wish to know more about Netskope and how it can assist your organisation in today’s SASE and Cloud based world then please get in touch with us here.







